SuperTokens Blog

February 13, 2026
Cheapest Auth0 Alternatives (2026): Open Source and Low-Cost Picks
Looking for the cheapest Auth0 alternatives? See free and low-cost options (OSS + managed), pricing gotchas, and when SuperTokens is the better fit.

January 26, 2026
What Is Better Auth and Who's It For?
Explore Better Auth's authentication features, its suitability for various projects, and key considerations for implementation.
January 17, 2026
FIDO2 vs U2F 5 Key Differences Explained
Understand the differences between FIDO2 and U2F. Learn how each works, where they apply, and which authentication standard to choose.
January 12, 2026
How to Migrate from Clerk Efficiently and Safely
Step-by-step guide on migrating from Clerk to SuperTokens—covering trickle, bulk import, export scripts, sessions, and security.

January 05, 2026
Frontegg vs. Auth0 vs. FusionAuth – Which Authentication Platform Fits Your Needs?
This guide breaks down what matters most when choosing between Frontegg, Auth0 and FusionAuth. We discusstheir strengths and limitations, and help you pick the one that fits your technical stack and business goals.
December 26, 2025
How Do I Add CAPTCHA to My Login Page?
Learn how to add CAPTCHA to login and signup pages, protect your app from bots, and see how SuperTokens makes it simple.

December 10, 2025
Best MFA Solutions Compared (2025 Guide)
Compare the best MFA solutions in 2025: features, costs, and trade-offs. Includes insights from SuperTokens’ MFA cost guide.

December 09, 2025
Passkey Examples: Real-World Use Cases and Implementation
Discover real-world passkey examples across Apple, Google, Coinbase, iPhone, PHP, and more, plus step-by-step implementation guidance.

December 05, 2025
Enterprise Identity Management What You Need to Know in 2025
Explore how enterprise identity management works, the challenges it solves, and what features modern orgs need for secure, scalable access control.

November 18, 2025
Deploying SuperTokens on Vercel with Next.js
Step-by-step guide to deploying SuperTokens authentication on Vercel with Next.js. Learn setup, environment config, API routes, and deployment tips.

November 02, 2025
Clerk Pricing - The Complete Guide
Deep dive into Clerk’s free & paid tiers, real cost examples, hidden fees, and comparison with Auth0/Okta for pricing clarity.

October 22, 2025
SolidJS Authentication: What Framework Should You Use?
Learn how to add secure authentication to SolidJS apps. Compare authentication frameworks and see why SuperTokens is a SolidJS-ready solution.
October 15, 2025
Auth0 vs FusionAuth (2025): Pricing, Hosting, Use Cases
Auth0 vs FusionAuth in 2025: pricing, hosting (SaaS vs self-host), DX, and best-fit use cases — plus an open-source alternative to consider.

October 15, 2025
Prompt Injection Attacks on LLMs: The Hidden AI Phishing Threat
Prompt injection attacks can trick LLMs into phishing users. Learn how invisible HTML is being weaponized—and how to protect your app’s auth flows.

October 14, 2025
WebAuthn Explained
A comprehensive guide to understanding WebAuthn, its benefits, and implementation details.

October 10, 2025
SuperTokens Launch Week 02: 7 Open-Source Auth Plugins
Open-source auth plugins you’ll reuse: profiling, banning, CAPTCHA, tenancy tools, and telemetry. React/Node ready.

October 10, 2025
Stytch vs Auth0 (2025): Pricing, Features, and More
Discover how Stytch and Auth0 compare in pricing, features, developer experience, and fraud tools — plus explore an open-source, self-hosted alternative that offers full control and transparency for modern authentication.

October 05, 2025
WorkOS Alternatives (2025): SSO, SCIM, and Pricing Compared
Discover the best WorkOS alternatives for SSO, SCIM, and audit logs — open-source and managed options, pricing signals, and when SuperTokens fits.
September 22, 2025
Biometric Web Authentication: What It Is and How to Use It
Understand biometric authentication on the web: how it works, use cases, security benefits, and how to implement it by using WebAuthn.

September 20, 2025
Add MFA to Next.js in Minutes by Using SuperTokens
Secure your Next.js app with multi-factor authentication fast. Learn how to add TOTP, email/SMS OTP, or passkeys using SuperTokens’ built-in MFA support.

September 20, 2025
OIDC vs SAML: Which Protocol to Use?
Compare OIDC and SAML for authentication use cases and see how SuperTokens lets you integrate both. Choose the right protocol for your app.

September 08, 2025
Magic Links Tutorial Secure Passwordless Login Made Simple
Learn how magic links work, their benefits, and how to implement them for secure, seamless passwordless authentication.

September 02, 2025
Firebase Pricing—The Complete Guide
Explore Firebase’s free vs Blaze tiers, real-world cost examples, hidden charges, and compare with Auth0/Okta for transparent pricing clarity.

August 30, 2025
OAuth Grant Types Explained: Which One Should You Use?
Confused by OAuth grant types? Learn how each one works, when to use it, and how SuperTokens simplifies implementation.

August 30, 2025
Why Startups Can't Afford Weak or Over-Engineered Authentication
Startups can't afford weak or overly complex authentication. Explore effective strategies to secure your business while keeping user experience seamless and efficient.
August 29, 2025
Understanding Authentication Protocols: Types and Security Measures
Explore various authentication protocols, their types, and delve into email authentication methods like SPF, DKIM, and DMARC to enhance security.

August 18, 2025
What Is a YubiKey and When to Use It vs. Authenticator Apps
Discover how YubiKeys work, when to choose them over authenticator apps, and how to integrate both in your auth flow.

August 15, 2025
What Is an Identity Provider and Why It Matters
Learn what an identity provider does, the business problems it solves, and how to implement one powerfully by using SuperTokens.

August 10, 2025
What Is B2B IAM?
Learn how B2B IAM helps businesses securely manage access for partners, vendors, and external users — plus what to look for in a modern solution.

August 08, 2025
Descope Pricing–The Complete Guide
Discover Descope’s pricing tiers, real-world cost examples, hidden fees, and how it stacks vs Auth0/Okta in CIAM pricing.

August 05, 2025
Stytch Pricing–The Complete Guide
Explore Stytch’s tiers, real‑world pricing examples, hidden fees, and comparison with Auth0/Okta for clear cost insights.
July 20, 2025
Fixing CORS Errors What They Are and How to Resolve Them
Learn what causes CORS errors, how they impact your web app, and how to fix them securely with proper headers and backend configurations.

July 09, 2025
SuperTokens Launch Week: Recap
With SuperTokens launch week 1 behind us, let's take a look at everything we've announced.

July 07, 2025
Top Open Source SSO Providers to Know in 2025
Compare the best open source SSO providers in 2025 and learn how to pick the right solution for your app’s security and scalability.
July 04, 2025
Rethinking our documentation
We rebuilt our documentation from the ground up—reorganizing structure, enforcing consistency, and making it easier than ever for developers to navigate and customize authentication with SuperTokens.

July 03, 2025
What Is Ping Identity and How Does It Compare?
Compare Ping Identity to Okta, ForgeRock, OneLogin, and SuperTokens. Honest feature breakdowns, use cases, and authentication strengths.

July 02, 2025
Bringing Secure Auth to AI: Introducing the SuperTokens MCP Toolkit
Seamlessly integrate authentication workflows into your LLM tools with the SuperTokens MCP Toolkit — a new way to bring real-time, secure auth context into AI-driven development.

July 01, 2025
Solving Auth for Everyone: The SuperTokens CLI Overhaul
We overhauled our CLI to be both a teaching tool and a real project starter—making it easier than ever to add auth to any stack, your way.

July 01, 2025
Revamping Onboarding at SuperTokens: A New Developer Experience from the Ground Up
Impressions matter—especially when it comes to onboarding. So we rebuilt the entire experience to deliver a setup flow that's intuitive, interactive, and tailored to your tech stack.

June 30, 2025
What is Authentication as a Service?
Discover how Authentication as a Service simplifies user authentication, enhances security, and scales with your application's needs.
June 30, 2025
RS256 vs HS256: Understanding the Difference in JWT Signing
Compare the RS256 vs HS256 JWT algorithms, understand key security differences, and find out which suits your application's needs.
June 30, 2025
SuperTokens Extensions: Customize Auth Your Way
Discover how SuperTokens Extensions bring modular, reusable, and powerful customization to authentication with a new plugin-based system.

June 27, 2025
SuperTokens Launch Week: Five Days of Auth Improvements
How we're making authentication easier to work with, one announcement at a time.

June 25, 2025
Passkeys vs Passwords – Which Is the Better Authentication Choice?
Explore the differences between passkeys and passwords in modern authentication. Learn why passkeys are more secure, user-friendly, and built for the future of login systems.

June 03, 2025
How to Integrate Clerk with Supabase (Plus another option for the curious)
🔐 Learn how to integrate Clerk with Supabase for powerful authentication and database management in your Next.js applications - with step-by-step tutorial and code examples.

May 23, 2025
What Is Authentication Bypass?
Learn what authentication bypass is, how attackers exploit it, and how to secure your apps against auth bypass vulnerabilities.

May 18, 2025
Angular Authentication
Learn how Angular authentication works, key methods to secure apps, and how to integrate with providers like SuperTokens or OAuth.

May 14, 2025
Auth0 SSO: Setup and Tips
Learn how Auth0 SSO works, where it falls short, and discover a simpler open-source alternative for modern authentication flows.

May 06, 2025
Implementing Phishing-Resistant MFA: Hands-On Developer Guide
Learn how to implement phishing-resistant MFA with FIDO2, WebAuthn, and SuperTokens. Step-by-step tutorial for secure, developer-friendly authentication.

April 30, 2025
What Is Step-Up Authentication? A Guide for Secure Access
An in-depth guide to step-up authentication—when to use it and how to implement it to secure high-risk actions in your app.

April 25, 2025
Top Auth0 Alternatives in 2025: The Best CIAM Solutions Compared | SuperTokens
Explore the top Auth0 alternatives for authentication and authorization. Discover solutions like SuperTokens, Okta, and Keycloak to find the perfect fit for your business needs.

April 21, 2025
Authelia vs Keycloak: Which One Suits You Best?
In today’s world of logins, passwords, and the eternal struggle to remember which one you used where, organizations are on the hunt for single sign-on (SSO) solutions that don’t just work but actually make life easier. Think security that doesn’t buckle under pressure, scalability that grows with you, and integrations that play nice with all your apps and systems—basically, the holy trinity of access control.

April 16, 2025
Breaking Down the Cost of Multi-Factor Authentication: Is It Worth It?
Explore the true cost of Multi-Factor Authentication (MFA), including licensing, integration, maintenance, and hidden risks. Learn how SuperTokens helps optimize MFA costs without compromising security.

April 15, 2025
What is Cloud-Based Authentication? A Detailed Guide
Cloud-based authentication refers to verifying user identities (often leveraging identity and access management, or IAM) and granting user access through services hosted offsite—often by dedicated identity providers—rather than keeping everything locked down on your own physical on-premises servers. This fundamental shift spares organizations from the headaches of provisioning hardware, configuring security solutions, and maintaining on-prem infrastructure. It also allows you to tap into more sophisticated authentication methods (like multi-factor authentication (MFA) or passwordless approaches) without massive up-front investments or complex, in-house integrations.

April 12, 2025
Enhancing Your Next.js Application with Middleware
Transform your Next.js app with middleware! Learn essential strategies to enhance functionality and streamline your development process today.

April 06, 2025
Credential Management: What It Is and Why It Matters
Learn about credential management, its importance, common security risks, and best practices. Discover how SuperTokens simplifies secure credential management.

April 02, 2025
Okta vs OneLogin: The Main Differences
Explore the differences between Okta and OneLogin to help you choose the right IAM solution.

April 01, 2025
How to Use Lambda Authorizers to Secure Your API Gateway
Learn how to secure your API Gateway using Lambda Authorizers with JWT. Discover setup tips, best practices, and integration steps for robust API security.

March 29, 2025
Mastering Next.js API Routes: The Developer's Guide to Backend Functionality
Learn how to create and optimize API Routes in Next.js, handle requests effectively, and integrate authentication with SuperTokens for secure backend operations.

March 25, 2025
4 Best 2FA Services for Developers to Secure Applications
Discover the best 2FA services for developers to secure applications with minimal friction. Compare top vendors and explore how SuperTokens simplifies 2FA integration.

March 18, 2025
Understanding Machine-to-Machine (M2M) Authentication: 2025 Guide
Explore the essentials of machine-to-machine authentication and best practices for implementing secure M2M communication.

March 18, 2025
SSO Examples: Real-World Use Cases and How to Implement Them
Explore real-world Single Sign-On (SSO) examples, use cases, and step-by-step implementation methods. Learn how tools like SuperTokens simplify SSO for developers.

March 16, 2025
Real World Examples of Multi-Factor Authentication
Security has always been crucial, especially in today’s digital landscape, where so much is at stake if security practices are weak or missing. The challenge with security is that the solutions and best practices are often logical and even obvious—yet, for various reasons, we sometimes choose to ignore them..

March 16, 2025
Okta vs Azure AD: Which IAM Solution Wins?
Explore the differences between Okta and Azure Active Directory (AD) to help you choose the right IAM solution.

March 10, 2025
7 Sneaky Ways Hackers Exploit Enumeration Attacks—and How to Stop Them
Discover the top 7 tactics hackers use in enumeration attacks and learn effective strategies to safeguard your authentication systems.
March 10, 2025
Top 7 NextAuth Alternatives for Secure Authentication [2024]
Authentication is the cornerstone of any secure application, and for many developers, NextAuth has been a go-to solution. Its ease of use and compatibility with Next.js make it a strong option for basic authentication needs. However, developers often encounter limitations with NextAuth, such as restricted customization, complex multi-platform integration, and insufficient support for advanced authentication protocols.

March 08, 2025
4 Best Firebase Alternatives for Scalable App Development [2025 Guide]
Discover the top Firebase alternatives, their features, and how they compare. Learn why SuperTokens is the best authentication solution for secure and scalable apps.

March 05, 2025
Top 8 Identity and Access Management Tools
Identity and Access Management (IAM) tools have become a cornerstone for businesses to securely manage user access across multiple systems and applications. With the growing threat landscape and increasingly complex compliance requirements, choosing the right IAM solution can significantly improve security, optimize user experiences, and simplify the lifecycle of identity management.

March 02, 2025
How to Set Up React User Authentication
User authentication forms the backbone of security in modern web applications, especially within the React ecosystem. Ensuring that only authenticated users can access specific parts of your application is crucial for safeguarding data integrity and access control.

February 27, 2025
Metadata in Next.js: Enhancing SEO and User Experience
Learn how to effectively manage metadata in Next.js to boost SEO and improve user engagement through static and dynamic configurations.

February 25, 2025
Pillars of a CIAM Strategy: Secure, Scale, and Personalize Customer Access
Explore the key elements of a successful CIAM strategy: ensuring security, scalability, and personalized access for your customers. Start optimizing now!
February 18, 2025
Multi-Tenant Architecture: Benefits, Practices & Implementation
This blog provides an in-depth exploration of how multi‑tenant SaaS architectures boost scalability, reduce costs, and enhance security through SuperTokens' innovative approach.

February 17, 2025
One-Time Password (OTP) Bots: How They Work and How to Defend Against Them
Explore how OTP bots bypass two-factor authentication (2FA), their growing threats, and strategies to protect your application using tools like SuperTokens.

February 15, 2025
SIM Swapping Is Hijacking Your User Accounts: How to Shut It Down
Learn about SIM swapping scams, their impact on personal security, and effective strategies to safeguard your mobile identity.

February 11, 2025
Webhook vs API: Key Differences and Use Cases
Explore the distinctions between webhooks and APIs, their functionalities, and determine the best scenarios for each in your integration strategy.

February 05, 2025
Top Password Cracking Techniques and How to Protect Against Them 🔐
Learn the most common password cracking techniques used by hackers and practical strategies to secure your accounts from such threats.

February 04, 2025
Top 8 Identity Management Solutions for Developers and Businesses
Discover the top 9 user management software tools for 2024! Streamline your processes and enhance security with our expert reviews and comparisons.

February 03, 2025
Integrating OAuth Providers for Seamless Authentication
Discover how to integrate OAuth providers for seamless authentication. Enhance user experience and security with our expert guides and resources.

January 28, 2025
Top Open Source Identity Management Systems
As cyber threats grow more sophisticated and compliance demands tighten, organizations are rethinking how they secure identities and control access. Traditional IAM solutions can be rigid, expensive, and opaque—leaving businesses locked into costly, one-size-fits-all models. Enter open-source IAM: a powerful, transparent alternative that puts control back in the hands of organizations. Offering unmatched flexibility, scalability, and security, open-source IAM is quietly reshaping the way enterprises safeguard their most valuable asset—identity. But is it the right fit for your business?

January 27, 2025
Choosing the Right Authentication Provider and API for Secure Applications
Learn how authentication providers and APIs secure modern applications. Explore features and integration tips to enhance user authentication and data protection.

January 27, 2025
What is IDP Authentication: How Identity Providers Secure Your Apps
Learn how IDP authentication works, why it’s critical for secure access management, and how to integrate tools like SuperTokens for seamless implementation.

January 27, 2025
What is Passwordless Authentication: The Cool Kid on The Block? 🔒🚫
What is passwordless authentication? Solve login challenges, explore methods, benefits, and tools for secure implementations.

January 20, 2025
What is Risk-Based Authentication? A Complete Guide
Learn how Risk-Based Authentication enhances security by adapting to user behavior and mitigating threats in real-time.
January 16, 2025
Simplify User Experience With Social Login
Social login has become a popular choice for modern apps looking to streamline the user authentication process. In this blog, we'll explore what social login is, how it works, its benefits and the challenges of implementing it

January 13, 2025
How to Build Effective Identity & Access Management Strategy
Discover how to develop an effective Identity and Access Management (IAM) strategy that secures sensitive data, ensures compliance, and streamlines user experiences.

January 13, 2025
Best 7 Okta Alternatives for Identity Management
Discover the top 7 Okta alternatives for identity and access management (IAM), including SuperTokens, Auth0, Ping Identity, and more. Compare features, pricing, scalability, and customization to find the best solution for your business needs.

January 07, 2025
How to implement OIDC with Microsoft Entra ID
Implementing OIDC with Microsoft Entra ID can be confusing. We're gonna help you implement it two different ways — in your own ExpressJS server or in SuperTokens.

January 05, 2025
Top 10 Passwordless Authentication Solutions in 2024
Discover the top 10 passwordless authentication solutions of 2024. Enhance your security and streamline user access with cutting-edge technologies today!

January 02, 2025
8 Benefits of Identity and Access Management (IAM) for Security
Discover the 8 key benefits of Identity and Access Management (IAM) for enhancing security. Learn how IAM can protect your organization effectively.

December 25, 2024
Keycloak Guide 2024: Pricing, Features, & Limitations 🔐
Discover Keycloak, a robust open-source IAM solution for enterprise-grade authentication needs like SSO, 2FA, and fine-grained access control. Compare it with SuperTokens, a lightweight, developer-friendly alternative for modern authentication requirements.

December 20, 2024
Token-Based Authentication for APIs: What It Is and How It Works
Discover how token-based authentication secures APIs with this simple guide. Understand its process, benefits, drawbacks and more.

December 17, 2024
10 Best Practices for Effective Identity and Access Management
Learn the top 10 Identity and Access Management (IAM) best practices to safeguard your organization from credential-based attacks. Explore common pitfalls like siloed systems, privilege creep, and manual provisioning, and discover how modern IAM solutions like SuperTokens help streamline security, ensure compliance, and boost productivity. Stay ahead with effective IAM strategies and protect sensitive data from evolving cyber threats.

December 17, 2024
Top 7 SSO Benefits for Enhanced Security [2024]
Discover the top 7 SSO benefits for 2024 to enhance your security. Learn how to protect your data and streamline user access effectively.
December 12, 2024
Token Based Authentication vs Session Based Authentication
Sessions vs. Tokens: Understanding the Differences in Authentication

December 11, 2024
Top Identity and Access Management Challenges
Discover how to tackle modern IAM challenges, from integration complexities to compliance, with actionable solutions and emerging trends like zero-trust and passwordless authentication. Learn how open-source tools like SuperTokens can future-proof your system in 2024.
December 09, 2024
How to Implement Identity and Access Management? [6 Steps]
Learn how to implement Identity and Access Management in just 6 steps. Enhance security and manage user access efficiently with our expert guide!
December 09, 2024
Unified Login: Because Who Doesn't Love a Good OAuth2 Adventure?
Ah, authentication. The bane of every developer's existence. Or is it? 🤔 Today, we're diving into the wonderful world of a new feature called Unified Login. Buckle up, folks—it's gonna be a wild ride!

December 02, 2024
A Comprehensive Guide to SSO Implementation 2024
This blog explores the benefits and functionalities of Single Sign-On (SSO), highlighting how it simplifies user authentication, enhances security, and integrates with modern identity management systems. It also covers how open standards like OAuth 2.0 and OIDC enable seamless access to applications, including the use of social logins from services like Google, Facebook, and Twitter.
November 28, 2024
7 Authentik Alternatives for Enhanced Identity Management in 2024
Explore 7 effective Authentik alternatives for improved identity management in 2024. Elevate your security measures and optimize user experience today.

November 26, 2024
Introduction to IAM Frameworks: Simplifying Access Management for Developers
Learn everything about Identity and Access Management (IAM) frameworks in this comprehensive guide.

November 18, 2024
A comprehensive guide to Django's user authentication system
Learn how to implement user registration, login/logout, permissions etc using Django's built-in user authentication system.

November 18, 2024
Session-Based Authentication: A Detailed Guide [2024]
Session-based authentication is a cornerstone of web security, providing a simple and controlled method to manage user sessions. This guide delves into its workings, advantages, and implementation, while addressing challenges like security vulnerabilities and scalability concerns.

November 15, 2024
9 SSO Best Practices to Strengthen Security in 2024
Discover the top 9 SSO best practices for 2024 to enhance your security. Learn how to protect your data and streamline user access effectively.

November 08, 2024
How Identity and Access Management Works: Detailed Guide
Discover the fundamentals, benefits, and best practices of Identity and Access Management (IAM) and how SuperTokens simplifies secure authentication and session management.

November 04, 2024
7 Common IAM Risks and How to Avoid Them
Reveal the 7 critical IAM risks that pose a threat to your business. Discover actionable advice to reduce these risks and strengthen your security measures.

November 04, 2024
Adding Authentication to Your Flask Backend with SuperTokens
Learn how to seamlessly add authentication to your Flask backend using SuperTokens. This guide covers setting up authentication with the SuperTokens CLI or manual configuration, enabling you to focus on building application logic instead of authentication infrastructure.

November 02, 2024
How to Authenticate and Authorize Users in a Node.js Express App
A step by step guide on how to Authenticate and Authorize Users in a Node.js Express App

October 16, 2024
"BuT, aUtH iS HaRd"
No, it's not. It's boring, red-tapey, a solved problem... but don't call it hard as a blanket statement.

October 15, 2024
Authentik Vs. Keycloak: Features and Experience Comparison
This blog compares Authentik and Keycloak, two popular open-source IAM solutions, highlighting their features, security, customization, and scalability. We break down which tool is best suited for different business sizes and needs, including an alternative, SuperTokens, for teams seeking a middle ground.
October 12, 2024
AuthO Vs. Clerk: Features, Pricing, And Pros & Cons
Explore a comprehensive comparison of Auth0 and Clerk, two leading authentication providers. Discover their unique features, pricing, and best use cases to help you choose the right tool for your project

October 10, 2024
Keycloak Vs. Okta: Features, Pricing, And Developer Experience
Choosing the right IAM solution is crucial for security and efficiency. This blog provides a clear comparison between Keycloak and Okta, examining features, customization, pricing, and developer experience. Learn which platform best suits your organization’s needs.

October 07, 2024
Hacktoberfest with SuperTokens
Celebrate Hacktoberfest with SuperTokens, learn how you can contribute to open source auth and get some goodies too!
October 07, 2024
How to use SuperTokens in a VueJS app with your own UI
Learn how to integrate supertokens-web-js SDK into your VueJS application.

September 28, 2024
Best Practices for Enterprise SSO
This guide will dive into what enterprise SSO is and why it’s necessary for modern organizations. It will also provide actionable tips for implementing it effectively

September 25, 2024
How to secure a NestJs Application
In this post, we will be using NestJS, a Node.js framework that excels at making backend development efficient and scalable. Inspired by mature frameworks like Spring and ASP.NET, NestJS brings the best practices from these proven systems into the JavaScript/TypeScript world.

September 20, 2024
What is FIDO
In this post, we’ll take you on a journey through the world of passkeys, breaking down their technical foundations and exploring how they work. We'll also look at the role of the FIDO2 and WebAuthn standards in shaping a future where passwords are no longer needed.

September 18, 2024
SuperTokens Customer Retrospective
A look back at how SuperTokens empowered clients across industries with flexible, secure authentication solutions. Explore key case studies and insights that shaped a year of innovation and success.
September 15, 2024
Anomaly Detection with SuperTokens
Learn about different attack vectors and how to safeguard your web app against them with SuperTokens attack prevention suite
September 10, 2024
7 Top Authelia Alternatives for Enhanced Authentication in 2025?
In this blog, we're going to look at the top 7 alternatives to Authelia. We’ll go over the main features, pricing, pros and cons of each option to help you decide what’s best for your authentication strategy.

September 01, 2024
How to use SuperTokens' pre built UI with VueJS
A step by step guide on how to integrate SuperTokens' pre built UI in a VueJS app
August 20, 2024
Demystifying SAML: A Comprehensive Guide
SAML is an authentication standard created to address the growing need of federated identity. In this blog we go over what SAML is and what makes it special.

August 19, 2024
Securing your Next.js with Authentication
This blog explains how to setup email password and social login with SuperTokens in Next.js.

August 16, 2024
Cookies vs. LocalStorage: Storing Session Data and Beyond
Learn about the best approach and common misconceptions of storing sessions in cookies or browser storage

August 15, 2024
7 Ways To Revoke JWT Tokens
Learn how to maintain a JWT token blacklist / deny list using an in-memory data cache

August 05, 2024
10 Benefits of Multi-Factor Authentication (MFA)
Traditional login mechanisms are plagued by security vulnerabilities and are susceptible to attacks. Multi-factor authentication bolsters security and mitigates a number of these vulnerabilities and has now become an industry standard.

August 02, 2024
What is a JWT? Understanding JSON Web Tokens
Explore JWT tokens: secure, compact credentials for modern web authentication. Learn how they work, their benefits, and best practices for implementing them in your applications.

July 20, 2024
OAuth vs JWT (JSON Web Tokens): An In-Depth Comparison
Explore the key differences between OAuth and JWT in this comprehensive guide. Learn when to use each, their pros and cons, and how they can work together for robust authentication.

July 17, 2024
Self-hosted Authentication
By self-hosting auth users gain finer control over their data.To shed some light on the matter, let’s compare several authentication providers which offer self-hosting functionality

July 15, 2024
Building a login screen with React and Bootstrap
Build an elegant login screen super fast using React and Bootstrap

July 13, 2024
How to Implement a Forgot Password Flow? Complete Guide
What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.

July 11, 2024
Top Auth0 alternatives: Auth0 vs Okta vs Cognito vs SuperTokens [2024]
An in depth review of Auth0 alternatives for 2024: Auth0 vs Okta vs Cognito vs SuperTokens
July 10, 2024
Setting up an authentication form with bootstrap in a Django application
This tutorial wil guide you on how you can setup a bootstrap login template in Django

July 10, 2024
OAuth2.0 vs SAML: The Best Security Protocol For Your App
SAML and OAuth are protocols often used in the authentication but what are the differences between them and which one do you choose?
July 07, 2024
What is Roles-Based Access Control (RBAC)?
Learn about RBAC and advantages + disadvantages compared to ABAC.
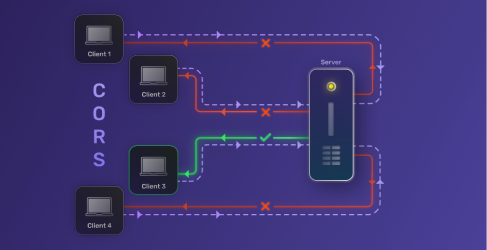
July 06, 2024
What is Cross Origin Resource Sharing (CORS)?
Cross-Origin Resource Sharing (CORS) is a mechanism that supports secure requests and data transfers from outside origins (domain, scheme, or port).

July 05, 2024
What is TOTP and why do you need it?
Time based one-time passwords solve a number of issues that plague traditional authentication methods. In this blog we break down TOTP and why it's so useful.

July 02, 2024
Okta Pricing: The Complete Guide [2024]
An in depth guide covering Okta's pricing model
July 01, 2024
Tips for Optimizing Your React App’s Performance
Poor app performance can reduce user engagement and will negatively affect SEO, here are tips to optimize your react app
June 28, 2024
Clerk Alternatives: Ceding vs. Owning UAM Control
An in depth guide covering Auth0's pricing model
June 27, 2024
Frontegg Alternatives For Greater UAM Flexibility & Control
Explore five top Frontegg alternatives for user access management, comparing features, pricing, and setup complexity to find the best fit for your needs. Discover the ideal UAM solution for your project.

June 26, 2024
Auth0 Pricing: The Complete Cost Breakdown [2024]
An in depth guide covering Auth0's pricing model
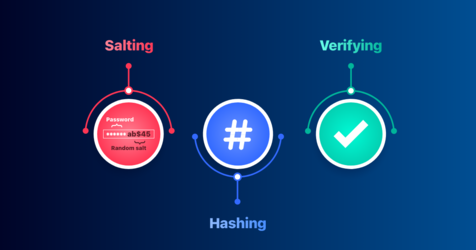
June 25, 2024
What is Password Hashing and why is it important
A guide on password hashing and salting in different languages and why it's important to do so
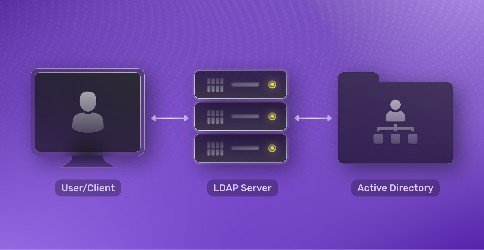
June 22, 2024
What is LDAP & How does it work?
In workforce identity and B2B flows, LDAP is main protocol used to interact with directory services that store user identity and device information. In this blog post we take a look at LDAP and how it works.
June 20, 2024
Comparing Keycloak Alternatives For Simpler User Authentication
We explore the differences between SuperTokens and Auth0 including their key features, pros and cons, and practical workflows. Whether you need full control with SuperTokens' self-hosted, open-source approach or the convenience of Auth0's managed service, this guide will help you choose the right authentication solution for your project.

June 16, 2024
Supertokens Vs AuthO: Self-Hosted Vs. Managed Solutions
Explore the core differences between SuperTokens and Auth0 including their key features, pros and cons, and practical workflows. Whether you need full control with SuperTokens' self-hosted, open-source approach or the convenience of Auth0's managed service, this guide will help you choose the right authentication solution for your project.

June 12, 2024
Supertokens Vs Keycloak: Going Custom Vs. Off-The-Shelf
Explore a high level comparison between two popular open-source authentication solutions, SuperTokens and Keycloak. This blog covers their key differences in architecture, configuration, UI, customizability, enterprise readiness, and more. Learn the advantages and disadvantages of each to determine which solution best fits your application's needs.
June 10, 2024
Features, Pricing, & Flexibility: Comparing AuthO Alternatives
This blog explores alternatives to Auth0, a leading IAM platform, highlighting options like SuperTokens, Okta, Firebase Authentication, AWS Cognito, FusionAuth, and Keycloak. It discusses key considerations such as pricing, customization, scalability, and integration, helping you choose the best authentication solution for your needs.
June 06, 2024
Stytch Alternatives For More Flexible User Access
This blog explores top Stytch alternatives for user access management, including SuperTokens, Auth0, and Firebase Authentication. We compare their features, flexibility, and pricing to help you choose the right solution. We also discuss open-source vs. proprietary systems and the benefits of building a custom security flow vs. using ready-made software.
June 04, 2024
Cognito Alternatives: Access Services That Pair With Any Set-Up
In this blog, we evaluate Amazon Cognito and compare it with five leading alternatives: SuperTokens, Clerk, Auth0, Stytch, and Frontegg. We'll cover pricing, setup complexity, data migration, and security features. Additionally, we discuss the benefits of open-source authentication and the choice between customized and out-of-the-box solutions. This guide helps you find the best user management solution for your needs.

June 03, 2024
AWS Cognito Pricing: The Complete Guide [2024]
An in depth guide covering AWS Cognito's pricing model

June 01, 2024
Clerk Vs SuperTokens: Custom Vs Ready-To-Use Access Protocol
Explore the differences between SuperTokens and Clerk to determine the best user access management solution for your project. Understand their core functionalities, key differences, and pricing to make an informed decision.

May 26, 2024
How To Use OIDC Tokens For More Efficient & Secure Login
Discover how to leverage OpenID Connect (OIDC) tokens to enhance your application's security without compromising user experience.Learn how to balance robust security measures with seamless user interactions, and get practical tips for integrating OIDC tokens into your authentication flow.

May 24, 2024
How the Heck Does OAuth Work?
In this blog we do a detailed technical overview of OAuth, explaining its evolution, various flows, and practical applications. It includes diagrams and real-world examples to enhance understanding.

May 17, 2024
Choosing The Right OAuth Grant Types For Your User
Discover the ins and outs of OAuth grant types and learn how to implement secure, user-friendly authentication flows. This comprehensive guide covers the different OAuth grant types, their best use cases, and practical tips for customizing your authorization flow.

May 16, 2024
Understanding & Using OAuth Tokens For Easy & Secure Login
Explore OAuth tokens in web security, their types, benefits, and best practices. Learn to implement and customize OAuth flows for optimal security and user experience.

May 14, 2024
What is OAuth and It's Importance in a Secure Web
Through this blog we hope to show you what OAuth is, explain how it works, and give you a sense of how OAuth can help your application.

May 09, 2024
2FA Authentication Providers
Passwords are not enough. Modern methods of attack have made passwords vulnerable to be stolen, this is where methods of enhancing security like 2FA and MFA come in

May 07, 2024
How To Streamline Access With Passwordless Authentication
A quick overview on how passwordless authentication can help streamline the login experience and increase user conversions

May 06, 2024
Balance Security & UX With Token Based Authentication
By minimizing the risk of credential theft, token based authentication grants users access to resources without the need to re-authenticate. In this blog we explore the balance between security and UX with Token Based Authentication

May 05, 2024
Best Single Sign-On Solutions for 2024
Discover the benefits and key features of Single Sign-On (SSO). Learn how SSO simplifies user experiences, enhances security, and meets enterprise needs. Explore popular SSO protocols like OAuth, SAML, and OpenID Connect, and compare top SSO providers

May 04, 2024
When & How To Build SSO Authentication For User Access
Learn how Single Sign-On (SSO) authentication simplifies user access to multiple applications with a single login, enhancing both security and user experience. Explore the benefits, protocols, and key differences between SSO and 2FA to optimize your authentication strategy.

May 01, 2024
Understanding Transport layer Security
In this article we explore TLS, it's vulnerabilities, and how to secure web communications against cyber threats
April 27, 2024
What is CSRF (Cross Site Request Forgery)
In this article we deep dive into the world of CSRF attacks, what they are and how to protect your application against them

April 18, 2024
2FA & MFA: Enhancing Security Without Compromising User Experience
Traditional authentication methods like email-password auth are the most at risk of being compromised during cyber attacks. However, overly complex authentication methods can frustrate users and hinder product adoption. In this blog we breakdown the pros and cons of adopting 2fa and mfa auth strategies

April 12, 2024
Types Of Authentication: Your Network Security Options
Although Password-based authentication is one of the most common authentication methods, they are the most at risk of being compromised during cyber attacks. In this blog we break down the types of authentication and how to choose the right type of authentication

April 10, 2024
Passkey Authentication: What Is It & How to Implement It
Discover the power of passkey authentication: a secure, user-friendly alternative to traditional passwords. Learn how passkeys work, their benefits over passwordless methods, and best practices for implementation to enhance your application's security and user experience.

April 05, 2024
Everything You Need to Know About 502 Bad Gateway Errors
Discover the ins and outs of 502 Bad Gateway Errors. From understanding the causes to troubleshooting steps and preventive measures, navigate through server communication breakdowns seamlessly.

April 03, 2024
OpenID Connect vs OAuth2: The Differences and How to Choose
Authentication and Authorization are the cornerstone of most modern software, but, these concepts are often misunderstood. In this blog we try to demystify those concepts and the accepted standards embodying them, that is OpenID Connect and OAuth 2

March 20, 2024
FedCM and how OAuth Flows are affected in the Post-Third-Party Cookie Era
Third Party Cookies have been synonymous with user tracking and privacy issues. In 2021 Google put forth a plan to retire third party cookies from chromium based browsers and put for the FedCM APIs. In this blog we will be discussing this change and what it means for traditional OAuth flows.

March 13, 2024
Phishing Attacks in 2024
Over the years phishing attacks have become more sophisticated than ever. In this blog we break down how phishing attacks have evolved and how you can safeguard against them
March 07, 2024
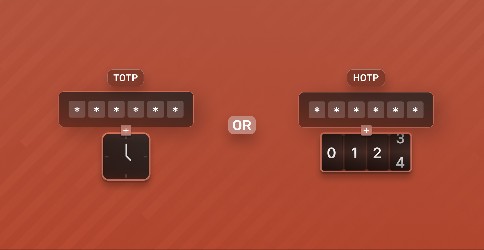
The difference between OTP, TOTP and HOTP
One time passwords are a more secure method of authentication. They remedy a number of issues which plague traditional username-password based authentication. But with methods like TOTP and HOTP it can be confusing. In this blog we break down these methods with their benefits and downsides

February 23, 2024
Understanding Authorization code flow with PKCE
Federated identity with OAuth is one of the most popular methods of implementing authentication. It lowers sign-up friction and is more secure than other auth methods like email-password based authentication.

February 20, 2024
All You Need To Know About the Zero Trust Model
Zero Trust is an IT security model that emphasizes identity verification for every person or device trying to access resources on a private network. In this blog we go over it's core principles and practical benefits.

February 16, 2024
What is SCIM Provisioning?
Managing identities can be a pain, in the past administrators would have to manually add identifying information needed by applications about users. This process takes longer and has a high margin of error. SCIM streamlines the management of user groups and devices. In this blog we will explore how it works.
February 13, 2024
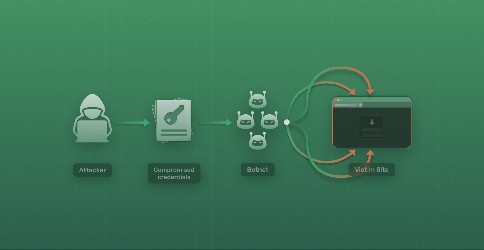
What is Credential Stuffing?
Most people are familiar with brute force attacks, where attackers attempt to guess passwords using characters at random paired with common password suggestions, but what is Credential Stuffing? In this we will go over this type of attack and how you can safeguard against it.
January 30, 2024
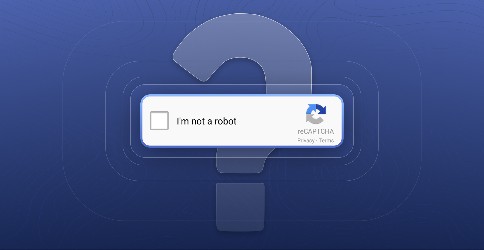
Navigating the Complex World of CAPTCHA Technology in Authentication
What is Captcha? Why is it needed? In this blog we will answer these questions and more

January 17, 2024
Unveiling the Intricacies of Local Storage and Session Storage
In this blog we delve into the workings of Local and Session storage breaking down the nuances that set them apart
December 11, 2023
Access Control for modern web applications
Access control plays a key role in protecting our data as we progressively move into an online society. In this blog we will explore the different types of access control and how they safeguard against attackers.
December 01, 2023
Multi-Tenant Authentication in 2024
Multi-tenant systems allow a single instance of a software application to serve multiple different tenants. This allows for a number of benefits that will be explored in this blog

October 01, 2023
How we used multi-tenancy to cut our AWS costs by 50%
Part 2 in a series of howe we were able to cut down our AWS infrastructure costs by more than 50%
September 28, 2023
How to create an invite-only auth flow in 2023
Invite only flows can drive exclusivity and enhance user engagement. In this blog we will go over how you can customize SuperTokens authentication to create an invite only flow
September 19, 2023
How we cut our AWS costs by more than 50%
Part 1 in a series of how we were able to cut down our AWS infrastructure costs by more than 50%
September 01, 2023
Demystifying HTTP Error Codes 401 vs 403
In this blog we will go over the http protocol error codes 401 and 403 and describe when is it appropriate to use each of them.

August 16, 2023
URI vs URL: The real difference between the two
In this blog we break down the differences between URL, URI, and URN

August 12, 2023
Why did HashiCorp adopt the Business Source License?
What is the Business Source License and why did HashiCorp adopt it?
August 08, 2023
Understanding JWKS (JSON Web Key Set)
JWKS are an important part of the authentication process. In this article we go over what they are and how they are used

August 02, 2023
Authentication vs Authorization: What's the difference?
Authentication and Authorization represent two fundamentally different aspects of security that work together in order to protect sensitive information. In this blog, we will go over some of the key differences between the two.

July 12, 2023
Migrating users without downtime in your service (The Lazy Migration Strategy)
User Migration can be a challenging process, in this article we go over some user migration scenarios and break down the lazy migration strategy
June 23, 2023
How we built a Chatbot that is an Expert at SuperTokens
Learn how we built a Q&A bot that is an expert at SuperTokens powered by ChatGPT

June 08, 2023
Ory vs Keycloak vs SuperTokens
Comparing the three leading open-source authentication providers - Ory, Keycloak and SuperTokens

April 17, 2023
OIDC vs OAuth
We break down the OIDC and OAuth standards and explain the key differences between the two

April 17, 2023
Testing SSO Implementation
A guide into single sign-on implementation and how to perform sso testing for authentication and login

March 16, 2023
Learnings from Revamping SuperTokens
A #buildinpublic piece on why we designed the SuperTokens homepage
February 24, 2023
Implementing the right Email Verification flow
Email verification can increase friction and adds another stop to onboarding, but when done correctly can lead to better security and establish better communication with users.
February 23, 2023
A Guide to Implementing Passwordless Login
Passwordless is one of the most popular authentication methods
January 16, 2023
Creating Great Authentication Experiences with Custom UI
A guide on creating great authentication experiences with custom UI

January 11, 2023
What do pre-built authentication UIs look like?
A comparison of the pre-built UIs from current authentication providers and how to customize them

January 09, 2023
SuperTokens 2022 Year in Review
2022 had been an amazing year for SuperTokens, here are some of the top highlights
October 27, 2022
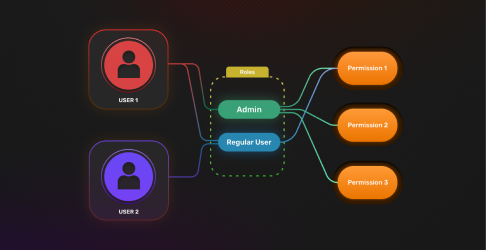
Introducing User Roles Authorization with SuperTokens
With user roles, you can now use SuperTokens to easily attach a different set of permissions to each user.

September 12, 2022
Protecting your Supabase app with SuperTokens authentication.
When building an app with Supabase you will have to choose an authentication solution. Here are some reasons why you should choose SuperTokens as you auth provider and why it pairs so well with Supabase
April 24, 2022
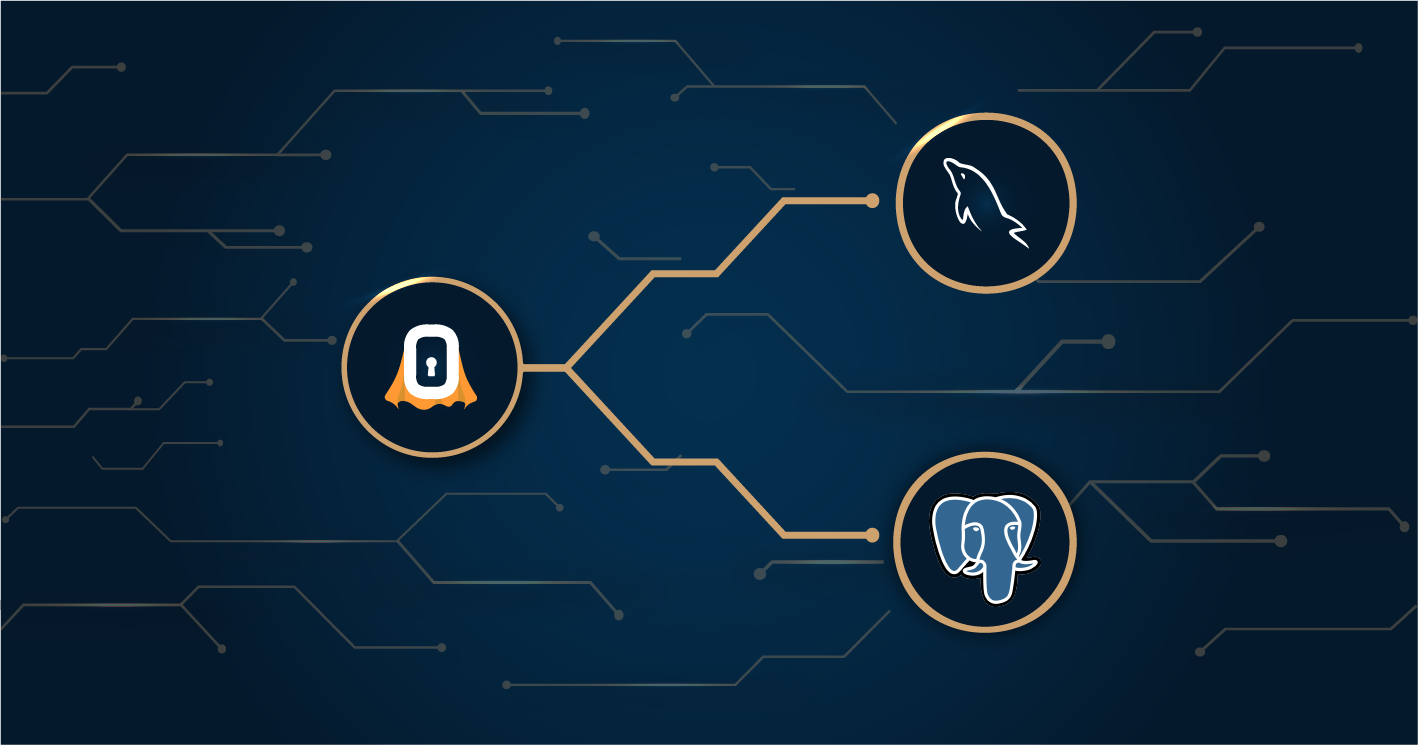
How to connect SuperTokens to a MySQL or to a PostgreSQL database
Learn how to connect a self-hosted SuperTokens core to a database with or without Docker

April 14, 2022
How to deploy SuperTokens with React and NodeJS on Vercel
This tutorial wil guide you on how to add SuperTokens to a React and Express app deployed on Vercel
February 09, 2022
How to Set up Social and Email Password Login With ReactJS in 10 Minute
In this blog, we'll walk you through setting up an email-password authentication with popular social providers like Google, GitHub, and Apple using SuperTokens on a ReactJS application with ExpressJS as the backend.
January 26, 2022
Adding social login to your website with SuperTokens (custom UI only)
This blog walks you through integrating your frontend with social login APIs provided by SuperTokens.

December 13, 2021
How to customise SuperTokens APIs
Any auth solution must provide the ability to customise their APIs. In this blog we discuss how to customise the auth APIs provided by SuperTokens using its “Override” feature
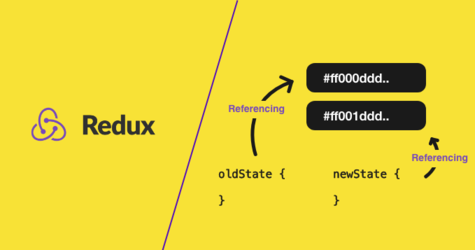
November 11, 2021
Why is redux state immutable?
This blog covers an analysis of why redux state is immutable and how you should go about modifying state in your Redux applications

November 10, 2021
Solve the problem of vendor lock-in
What is vendor lock-in? How does it affect your customers? What are the different ways you can minimize it? Read the blog to learn more.

March 05, 2021
The real reason Okta spent $6.5B on Auth0
Why did Okta spend $6.5B on Auth0? What does this mean for app developers? See reactions from customers and employees

December 10, 2020
Speed up your web development time by integrating Webflow into a React application
Writing JSX to build pixel perfect UI elements can be very time consuming and frustrating. Learn how react engineers can inject complex elements / React components into a Webflow generated HTML page.
July 30, 2020
Detecting session hijacking using rotating refresh tokens - OSW 2020
Session hijacking is one of the oldest, yet unsolved, attack vectors to gain unauthorised access to a user’s account. This discussion is regarding a method called "rotating refresh tokens" to better detect token theft.

June 11, 2020
Express-session vs SuperTokens for handling user sessions
This article will be comparing SuperTokens to Node’s most popular session management library– express-session. Learn more about the comparison based on different security and performance metrics.
May 06, 2020
Should you use Express-session for your production app?
Being Node’s most popular session management library, express-session has its set of flaws– especially when it comes to security. This article will help you analyse the good and bad parts of it.

April 24, 2020
OAuth 2.0 vs Session Management
A lot of developers confuse OAuth with web session management and hence end up using the wrong protocol. This article will clarify when to use what solution.

March 18, 2020
Are you using JWTs for user sessions in the correct way?
JWTs were originally designed for use in OAuth. This article covers the pros and cons of using JWT and talks about a solution which has the advantages of JWTs without any of its disadvantages.
June 08, 2019
The best way to securely manage user sessions
This blog covers an analysis of a new open source session flow that is secure and easy to integrate. Learn more about the customizable library and its implementation details.
June 07, 2019
All you need to know about user session security
This article covers extensive conversations with over 70+ developers exploring different session management practices, identifying issues and converging on a solution to these issues.