Table of Contents
- Introduction
- The Importance of Mitigating Risks in Identity and Access Management
- Common IAM Risks and Strategies to Avoid Them
- The Need for a Comprehensive IAM Strategy
- SuperTokens: The Solution to Key IAM Challenges
- Frequently Asked Questions About IAM Risks
- Conclusion
Introduction
Managing user identities and access rights is becoming quite a challenge. With more people working remotely and organizations using cloud services, it’s more important than ever to keep track of who has access to what. This is where Identity and Access Management (IAM) comes in.
IAM is all about making sure that the right people have access to the right resources at the right times. Think of it like a digital gatekeeper—it helps protect sensitive information by controlling who can enter and access what. However, with this responsibility comes some big risks that organizations need to be aware of and tackle head-on.
This guide will break down some of the most common IAM risks and their possible effects. Plus, it will offer practical strategies to mitigate those risks, helping organizations strengthen their security measures and keep their data safe.
The Importance of Mitigating Risks in Identity and Access Management
The consequences of poorly managed IAM systems can be severe and far-reaching. According to a recent IBM Security report, the average cost of a data breach reached $4.88 million in 2024, with compromised credentials being a leading cause. For security-conscious organizations, the impact of unmanaged IAM risks can manifest in several critical ways:
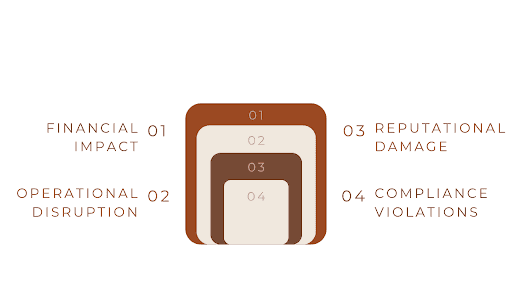
- Financial Impact: Beyond immediate data breach costs, organizations face potential regulatory fines, legal expenses, and lost business opportunities.
- Reputational Damage: Trust is paramount; once broken due to a security incident, rebuilding customer confidence can take years.
- Operational Disruption: Inadequate access controls can lead to workflow bottlenecks and reduced productivity.
- Compliance Violations: With regulations like GDPR and CCPA enforcing strict data protection requirements, IAM failures can result in significant penalties.
Common IAM Risks and Strategies to Avoid Them
Here are seven prevalent IAM risks along with actionable strategies to mitigate them:
1. Excessive User Privileges
Excessive user privileges occur when employees or systems are granted more access than they require to perform their job functions. This issue is a frequent oversight, often stemming from “permission creep,” where users accumulate access rights over time without review or revocation. While this may seem harmless initially, it creates vulnerabilities that attackers or malicious insiders can exploit.
Impact: Increased potential damage from compromised accounts and insider threats.
How to Avoid:
- Implement Role-Based Access Control (RBAC) to align permissions with job functions.
- Conduct quarterly access reviews to identify and revoke unnecessary privileges.
- Use automated tools to detect and alert privilege escalations.
- Document and justify all privilege assignments.
2. Weak Password Policies
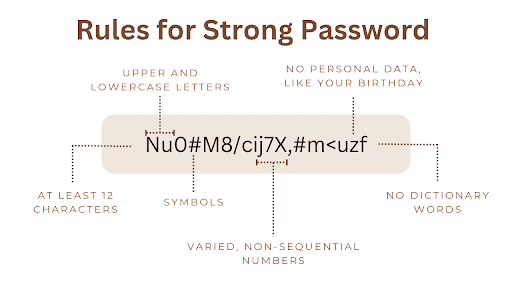
Weak password policies are a major issue in cybersecurity. Even though there are better ways to authenticate users now, many companies still depend on passwords and don’t have strong enough security measures in place. Some common problems are allowing short passwords, not requiring regular updates, and not blocking common phrases or patterns.
When passwords are weak, it’s not just bad news for the company; it can also hurt customer trust, especially if their data gets leaked. Improving password policies is one of the easiest and most effective ways to strengthen identity and access management systems.
Impact: Weak passwords provide attackers with an easy entry point into organizational systems.
How to Avoid:
- Enforce strong password requirements (length, complexity, history).
- Implement Multi-Factor Authentication (MFA) across all systems.
- Use password managers to encourage unique passwords.
- Provide regular password security training for employees.
3. Lack of Visibility and Monitoring
IAM visibility refers to an organization’s ability to monitor access patterns, detect anomalies, and audit changes across its user base. Without adequate visibility, it becomes nearly impossible to identify unauthorized access attempts or trace the origins of suspicious activity. This blind spot is a critical vulnerability, especially in environments with complex infrastructures or frequent system integrations.
On average, companies take 197 days to identify and 69 days to contain a breach, according to IBM. Proper IAM monitoring can help reduce this time, potentially saving millions of dollars.
Impact: Without proper visibility, organizations can’t detect unauthorized access attempts or suspicious behavior patterns until it’s too late.
How to Avoid:
- Deploy Security Information and Event Management (SIEM) solutions.
- Implement User and Entity Behavior Analytics (UEBA).
- Create automated alerts for suspicious activities.
- Maintain detailed access logs and conduct regular reviews.
4. Inadequate Offboarding Processes
Employee transitions are a normal part of business, but offboarding is often neglected when it comes to security. If organizations don’t quickly revoke access after an employee leaves, their systems can be at risk of unauthorized use.
In many cases, ex-employees unintentionally retain access due to outdated directories or inefficient HR-IAM integration. However, this oversight creates significant risks, including potential sabotage, data theft, or compliance breaches, particularly in industries handling sensitive information.
Impact: Former employees retaining access creates significant security risks and potential compliance violations.
How to Avoid:
- Create automated offboarding workflows.
- Implement Just-in-Time access provisioning.
- Regularly audit dormant accounts.
- Maintain up-to-date user directories integrated with HR systems.
5. Misconfigured IAM Policies
IAM misconfigurations often happen because digital transformation is happening so fast. As we adopt more cloud services and integrate different systems, managing policies becomes more complicated. Sometimes, these misconfigurations can accidentally give too much access to sensitive information or limit access for legitimate users, which can mess up workflows and cause compliance problems.
Gartner predicts that through 2025, 99% of cloud security failures will be the customer’s fault. Misconfigurations, including those in IAM, are significant contributors to these failures.
Impact: Misconfigured policies can inadvertently expose sensitive resources or prevent legitimate access to critical systems.
How to Avoid:
- Use policy validation tools.
- Implement configuration management best practices.
- Conduct regular security assessments.
- Maintain detailed documentation of IAM policies.
6. Shadow IT Risks
Shadow IT refers to the use of unauthorized applications or systems by employees, bypassing approved IAM frameworks. This practice has surged in the era of remote work, with employees turning to third-party tools to boost productivity without considering security implications.
When organizations don’t know about these applications, it’s harder to keep track of data and enforce security rules. This can lead to data leaks, security breaches, or problems with compliance. To handle shadow IT effectively, companies need to find a way to allow employees to use useful tools while still keeping their data safe.
Impact: Unauthorized applications create security blind spots and increase the risk of data leakage.
How to Avoid:
- Implement Cloud Access Security Broker (CASB) solutions.
- Create clear policies for application usage.
- Provide approved alternatives to common shadow IT applications.
- Conduct regular employee training on security risks.
7. IAM System Outages
IAM outages are more than an inconvenience—they can bring entire operations to a standstill. As IAM systems handle authentication for critical applications, any downtime disrupts workflows and leaves organizations scrambling for alternatives.
The risks extend beyond operational delays. In many cases, outages force employees to use unsecured workarounds, such as shared credentials or local copies of sensitive files, further compromising security. Preventing outages involves not only robust infrastructure but also ongoing testing and monitoring to ensure resilience.
Impact: System downtime can paralyze operations and force unsafe workarounds.
How to Avoid:
- Implement high-availability architectures.
- Regularly test backup and disaster recovery plans.
- Monitor system health proactively.
- Maintain documented incident response procedures.
The Need for a Comprehensive IAM Strategy
A robust IAM strategy requires more than just implementing technical controls. Organizations need to adopt a holistic approach that combines technology, processes, and people. This includes regular training, clear policies, and the right tools to manage and monitor access effectively.
Modern IAM solutions like SuperTokens provide the foundation for implementing these strategies effectively. With features designed to address common IAM challenges, organizations can significantly reduce their risk exposure while improving operational efficiency.
Remember: Security is not a destination but a journey. Stay vigilant, stay updated, and keep your IAM infrastructure robust and resilient.
SuperTokens: The Solution to Key IAM Challenges
SuperTokens offers a comprehensive approach to addressing IAM risk. The platform provides:
- Granular Access Control: Define precise roles and permissions to ensure users access only the resources they need, reducing the risk of unauthorized access or data exposure.
- Security Best Practices Built-In: Leverages industry-standard protocols to defend against common vulnerabilities like SQL injection and cross-site scripting.
- Detailed Audit Logging: Monitor user activities and system changes to support compliance and streamline security investigations.
- Reliable Scalability and Availability: Maintain seamless operations during high traffic, with the flexibility to scale as user demand grows.
- Administrator-Friendly Interface: Simplify user and security management with an intuitive and easy-to-navigate dashboard.
- Seamless System Integration: Effortlessly connect with existing workflows and infrastructure for streamlined implementation.
- Customizable Authentication UI: Personalize authentication workflows to reflect brand identity, enhancing user confidence.
- Multi-Factor Authentication (MFA) Support: Strengthen security by adding extra identity verification steps, reducing risks of unauthorized access.
Frequently Asked Questions About IAM Risks
What is IAM safety?
IAM safety refers to the security measures and controls implemented to protect digital identities and manage access to resources. It encompasses authentication, authorization, and accounting (AAA) to ensure only legitimate users can access appropriate resources.
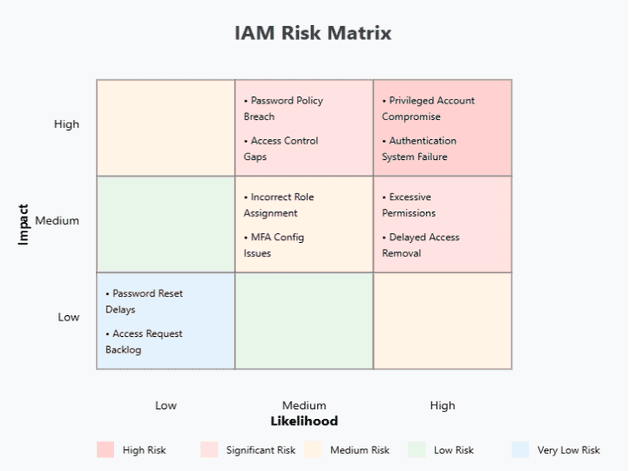
What is the risk matrix in IAM?
A risk matrix in IAM helps organizations evaluate and prioritize potential security threats based on their likelihood and potential impact. This tool aids in resource allocation and risk mitigation planning.
What are IAM conditions?
IAM conditions are specific criteria that must be met before access is granted. These can include time-based restrictions, IP address limitations, device requirements, or multi-factor authentication completion.
How to calculate the risk?
IAM risk calculation involves assessing both the probability of a security incident and its potential impact. Organizations typically use metrics such as:
- Number of privileged accounts
- Failed login attempts
- Time to revoke access
- Policy violation incidents
Conclusion
As organizations continue to digitally transform, the importance of robust IAM practices cannot be overstated. By understanding and addressing common IAM risks, organizations can better protect their assets while ensuring efficient operations.
The key to success lies in adopting a proactive approach to IAM risk management, implementing appropriate tools and controls, and maintaining vigilance through regular assessments and updates. Modern solutions like SuperTokens offer comprehensive authentication and identity management capabilities through their self-hosted authentication solution that can help organizations build a strong foundation for their IAM strategy. With the right combination of tools, processes, and ongoing oversight, organizations can effectively mitigate common IAM risks and maintain a strong security posture.
Secure your organization with SuperTokens and follow best practices for risk management. Signup today!