Table of Contents
- SAML vs OAuth: Comparison Overview
- What is SAML?
- What is OAuth?
- Key Differences Between SAML and OAuth
- Advantages and Disadvantages of SAML
- Advantages and Disadvantages of OAuth
- When to Use SAML
- When to Use OAuth
- Conclusion
- Frequently Asked Questions about SAML & OAuth
SAML vs OAuth: Comparison Overview
| Dimension | SAML | OAuth |
|---|---|---|
| Primary Use | Single Sign-On (SSO) for enterprise | Authorization for applications |
| Protocol Standards | XML-based | JSON and HTTP-based |
| Workflow | Identity assertion | Access delegation |
| SSO | Yes | Yes, but more for authorization |
| Typical Use Cases | Internal enterprise applications | Public APIs, third-party services |
What is SAML?
Definition of SAML (Security Assertion Markup Language)
SAML, or Security Assertion Markup Language, is an XML-based framework that facilitates the exchange of authentication and authorization data between different security domains. Its primary purpose is to enable Single Sign-On (SSO) for enterprise applications, providing a seamless and secure user authentication experience.
How SAML Works
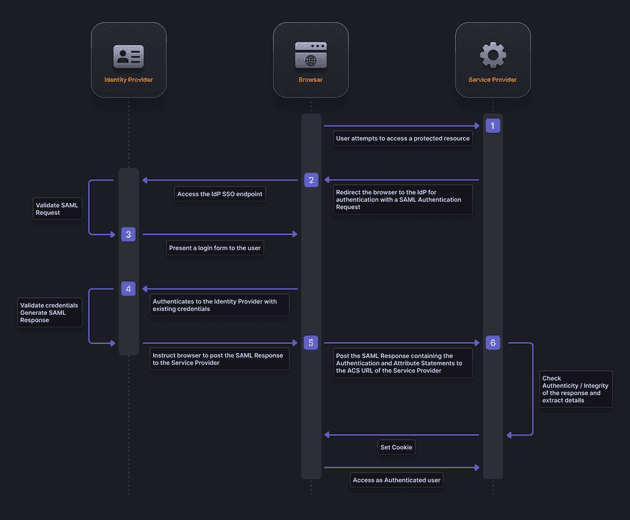
SAML works by exchanging user information, such as logins, authentication state, identifiers, and other relevant attributes between the identity and service provider. As a result, it simplifies and secures the authentication process as the user only needs to log in once with a single set of authentication credentials. So, when the user tries to access a site, the identity provider passes the SAML authentication to the service provider, who then grants the user entry.
The interaction can be broken down into three main components: the user (principal), the identity provider (IdP), and the service provider (SP). Here’s a simplified workflow of how SAML operates:
- User Access: The user attempts to access a resource on the service provider’s site.
- Request for Authentication: The service provider sends an authentication request to the identity provider.
- User Authentication: The identity provider authenticates the user, usually via credentials like username and password.
- Assertion Creation: Upon successful authentication, the identity provider creates a SAML assertion, an XML document containing the user’s authentication information.
- Assertion Transmission: The identity provider sends the SAML assertion to the service provider.
- Assertion Verification: The service provider verifies the assertion’s authenticity and integrity.
- Access Granted: Once verified, the service provider grants the user access to the requested resource.
What is OAuth?
Definition of OAuth (Open Authorization)
OAuth, or Open Authorization, is an open standard for access delegation commonly used to allow internet users to grant websites or applications limited access to their information without exposing their passwords. It is widely used for authorizing third-party applications to access user data from services like Google, Facebook, and Twitter.
How OAuth Works
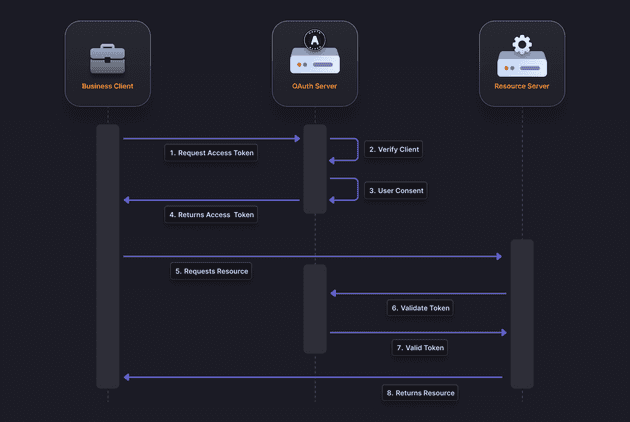
OAuth operates through a series of steps involving the user, the application (client), the authorization server, and the resource server. The process can be summarized as follows:
- Authorization Request: The user initiates a request to access a resource via the application.
- Authorization Grant: The application redirects the user to the authorization server, where the user authenticates and grants permission.
- Access Token: The authorization server issues an access token to the application.
- Resource Request: The application uses the access token to request the resource from the resource server.
- Resource Access: The resource server validates the access token and provides the requested resource to the application.
Key Differences Between SAML and OAuth
Difference 1: Primary Use
- SAML: Primarily used for Single Sign-On (SSO) within enterprise environments, enabling users to authenticate once and gain access to multiple applications.
- OAuth: Designed for authorization, allowing third-party applications to access user data without exposing credentials.
Difference 2: Protocol Standards
- SAML: Utilizes XML for message formats and relies on complex, verbose XML schemas.
- OAuth: Uses JSON for message formats, making it lightweight and more suitable for web and mobile applications.
Difference 3: Workflow
- SAML: Focuses on identity assertion, ensuring that the user is authenticated by the identity provider and that this authentication is communicated to the service provider.
- OAuth: Emphasizes access delegation, where the user grants the application permission to access resources on their behalf, without sharing their credentials.
Advantages and Disadvantages of SAML
Advantages
- Enterprise SSO: SAML is ideal for SSO in enterprise environments, allowing users to access multiple applications with a single set of credentials.
- Security: SAML’s XML-based assertions provide robust security features, ensuring secure transmission of authentication data.
- Interoperability: Widely supported and used in various enterprise applications and services.
Disadvantages
- Complexity: Implementation and maintenance can be complex due to the detailed XML schemas and extensive configuration requirements.
- Performance: The verbose nature of XML can lead to performance overhead, especially in large-scale implementations.
Advantages and Disadvantages of OAuth
Advantages
- Simplicity: OAuth’s use of JSON and HTTP makes it simpler to implement and integrate compared to SAML.
- Flexibility: Suitable for a wide range of applications, including mobile and web, due to its lightweight nature.
- Third-Party Access: Excellent for granting third-party applications access to user data without compromising security.
Disadvantages
- Authorization Focus: Primarily designed for authorization, not authentication, which can lead to confusion if used for login purposes.
- Security Risks: If not implemented correctly, OAuth can be susceptible to various security vulnerabilities, such as token theft.
When to Use SAML
- Enterprise SSO: When implementing Single Sign-On for internal enterprise applications.
- Internal Applications: When strong security and detailed user information exchange are required within an organization.
When to Use OAuth
- Third-Party Applications: When granting access to external or third-party applications, such as social media logins.
- Public APIs: When providing access to public APIs and needing to delegate access control securely.
Conclusion
SAML and OAuth serve distinct purposes and are tailored for different scenarios. SAML excels in enterprise SSO environments, providing robust security and interoperability for internal applications. OAuth shines in scenarios requiring secure access delegation for third-party applications and public APIs. Understanding the strengths and use cases of each protocol is crucial for selecting the right one for your specific needs.
Frequently Asked Questions about SAML & OAuth
What is the main difference between SAML and OAuth?
The main difference is in their primary use: SAML is mainly used for authentication and Single Sign-On (SSO), while OAuth is used for authorization and access delegation.
Can OAuth be used for authentication?
OAuth can be used for authentication, but it is not its primary purpose. For authentication, OAuth is often paired with OpenID Connect, which builds on OAuth to provide authentication capabilities.
Is SAML more secure than OAuth?
Both SAML and OAuth have strong security features, but their security depends on proper implementation. SAML’s XML-based assertions provide robust security for SSO, while OAuth’s token-based approach is secure for access delegation if implemented correctly.
Which protocol is better for mobile applications?
OAuth is generally better suited for mobile applications due to its lightweight nature and use of JSON and HTTP, which are more efficient for mobile data exchange.
How does SSO work in SAML?
SSO in SAML works by allowing users to authenticate once with an identity provider and then access multiple service providers without re-authenticating, using SAML assertions to convey authentication information.
What are some common use cases for OAuth?
Common use cases for OAuth include social media logins, where users can log in to a third-party application using their social media credentials, and accessing public APIs, such as integrating third-party services with user data.