You finally switched to Two-Factor Authentication (2FA), feeling secure and ahead of the game. But just as we start winning, cybercriminals move the goalpost by introducing OTP bots.
OTP (One-Time Password) bots are automated software, most often designed to be malicious (crimeware-as-a-service), designed to bypass 2FA and steal access to user accounts. They are most often sold through Telegram, a texting app.
Now imagine you’re yelling at your game controller because the NPC just betrayed you in the worst way, when you receive a text from your bank. “We’ve detected suspicious activity. Reply with the OTP we just sent to secure your account.”
Panicked (and wanting to get back to your game), you comply and are unaware you’ve just handed over your account to a cyber cockroach scuttling through security flaws. 🪳🔓
This is what a typical OTP bot attack can look like. These attacks are getting smarter, targeting individuals, employees, and even entire businesses. But don’t worry. We don’t back down from challenges. 🥊
Let’s break down how OTP bots work and, more importantly, how to fight them.
Understanding Two-Factor Authentication (2FA) & One-Time Passwords (OTPs) 🔐📲
A Two-Factor Authentication (2FA) is a second layer of authentication for added security, very commonly a One-Time Password (OTP).
Authentication generally falls into three categories:
✅ Something you know (your password)
✅ Something you have (your phone)
✅ Something you are (your fingerprint or face)
Your password is the first layer of security (something you know), but 2FA strengthens this by requiring a second factor, typically an OTP sent to your phone (something you have) or biometric verification (something you are).
Why 2FA Matters
🔴 Without 2FA: A hacker only needs to steal your password to access your account.
🟢 With 2FA (OTP Layer): Even if your password is compromised, an attacker still needs the second authentication factor, making unauthorized access much harder.
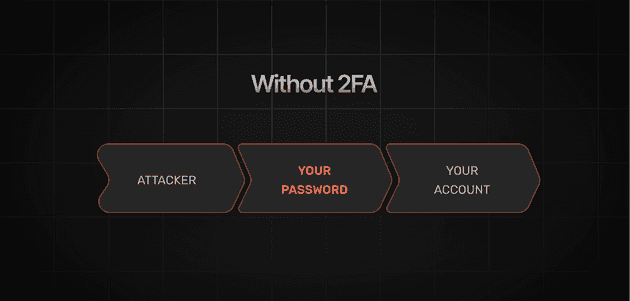
Without 2FA, stealing your password is all it takes for an attacker to access your account.
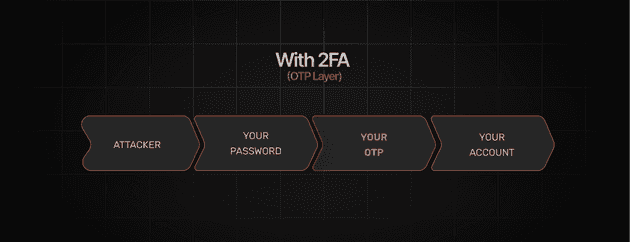
With 2FA, having the second layer of authentication (the OTP) prevents a hacker from accessing your account even if they have your password.
What Are OTPs?
A One-Time Password (OTP) is a temporary and time-sensitive code sent to you via an app, SMS, or email to verify a login attempt. Even if a hacker steals your password, they still need this unique code, which adds a crucial extra layer of security to your account.
For years, we’ve been told that OTP-based 2FA is the ultimate defense. Many apps now push users to enable it, giving us a reassuring sense of security.
But here’s the catch, cybercriminals have found a way around it.
Welcome to the world of OTP bots where attackers use automation to bypass 2FA and steal access to accounts. Let’s dive into how they work and, more importantly, how to stop them. 🚨🥊
What Are OTP Bots? 🤖
OTP bots are advanced programs designed to intercept and steal One-Time Passwords (OTPs), allowing attackers to gain unauthorized access to protected accounts. Their rise coincides with the growing use of Two-Factor Authentication (2FA). OTP bots are considered to be a form of social engineering.
These bots cause significant harm to both individuals and businesses. Industries like banking, e-commerce, and SaaS platforms are frequent targets for OTP bots because they often store sensitive user information, including payment details.
Most OTP bots are purchased by attackers on platforms like Telegram. They are designed to be very easy to implement.
It’s important to note that falling for social engineering doesn’t mean you’re careless. Attackers are aware of growing security awareness and craft their tools to exploit even cautious users.
SMSRanger is one of the most popular OTP bots currently in operation. It began during the pandemic when most people were working from home. The attacker can select a package to purchase and make the payment to the company providing the bot. It’s as simple as that.
How Do OTP Bots Work? 🔍
OTP bots use a combination of automation and social engineering tactics to wreak havoc upon your systems.
A Diagram of How An OTP Bot Attack Generally Works
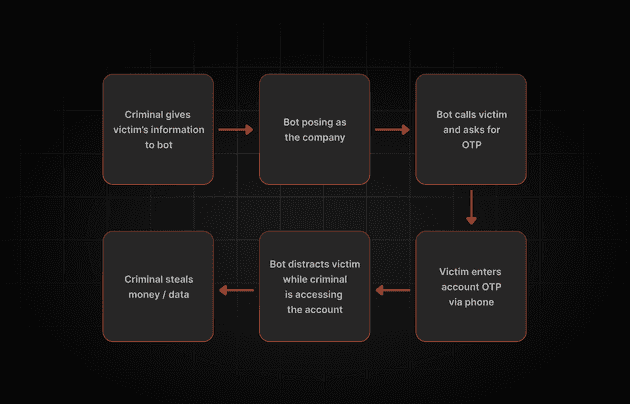
In the above diagram, the attacker does the account takeover (ATO), but some OTP bot services offer to do that as well.
The script an OTP bot uses can be completely customizable, from the language used to the music they play when you are on hold.
Steps to an OTP Bot Attack
- Attacker Initiates the Attack – Armed with a stolen password (from phishing, data breaches, or credential stuffing), the attacker hands it over to an OTP bot.
- Bot Impersonates a Trusted Entity – The bot calls or texts the victim, pretending to be a legitimate company (like a bank or service provider) and warns them about a suspicious transaction.
- Victim Falls for the Trap – Believing the message is real, the victim provides the OTP they just received, thinking they’re securing their account.
- Bot Completes the Attack – While keeping the victim engaged, the bot forwards the OTP to the attacker, who swiftly logs in and gains unauthorized access, often stealing money or sensitive information in seconds.
Common Tactics Used by OTP Bots
Understanding these tactics is key to defending against them. Let’s break down how you can stay protected. 🔐
🧠 Exploiting Human Vulnerabilities
The biggest weakness OTP bots exploit is human error. Using social engineering, attackers trick users into willingly sharing their OTPs. Since people are used to entering or sharing codes, they’re less likely to question a request, especially if the attacker convincingly impersonates a trusted source, like a bank or SaaS platform.
📲 Real-Time OTP Interception
Attackers can intercept OTPs in real-time using techniques like phishing or malware. Once they capture your password, they immediately prompt for an OTP, ensuring they can log in before the code expires. A big reason why real-time OTP interception is possible is because of vulnerabilities in the SS7 (Common Channel Signaling System No. 7) protocol, which powers most of our network communication worldwide.
🤖 Automated Call Bots
Sophisticated bots make automated phone calls, posing as legitimate organizations, and manipulate victims into providing OTPs. The urgency and professionalism of these calls often catch users off guard. The nature of automated calls also makes them insanely scalable, allowing more attacks to be done in a short period of time.
🔑 Credential Stuffing with OTP Prompts
Attackers use stolen credentials from data breaches and attempt to log in on multiple sites. If 2FA is enabled, they trigger OTP prompts and use bots or social engineering to collect the codes, completing the login process.
Types of OTP Bots & Their Sneaky Tactics 🤖💀
Voice Bots
Automated calls impersonate real people and organizations using AI-generated voices, accents, and languages to sound convincing.
SMS Bots
Fake texts mimic official messages, use number spoofing, and even exploit SS7 vulnerabilities to intercept OTPs.
App-based Bots
Exploit authentication apps, tricking users into entering OTPs into fake interfaces or abusing security flaws.
Email Phishing Bots
Send realistic emails using domain spoofing and personalized content to trick victims into sharing OTPs.
Social Media Bots
Use public info to craft convincing scams, impersonating friends, companies, or influencers to steal OTPs.
Browser Based Bots
Inject malicious scripts to intercept OTPs or alter website appearances in real-time, fooling users.
API-Exploiting Bots
Target insecure APIs, intercepting OTPs before they reach the verification system.
Why OTP Bots Are a Growing Threat 👾
As OTPs become a key security feature in 2FA and passwordless login systems, they also become a target for hackers to exploit.
The more businesses and users begin to rely on OTPs to secure their accounts, the more attackers will continue to focus on bypassing this layer of security, like they have done with passwords.
Additionally, hackers don’t need superhacking skills anymore, like some sort of hacker supervillains, to launch their attacks. OTP bot services are readily available for them to purchase. These services have made it easier for attackers to launch their attacks with minimal effort and cost.
So this combination of widespread OTP usage and easy access to hacking tools makes OTP bots a serious threat to users and the businesses their accounts are on.
Security Risks Posed by OTP Bots
OTP bots pose immense risk to businesses and users, so both need to act urgently in protecting their data and information.
According to a Proofpoint report, attackers launch over 100,000 phone-based attacks daily. The growing use of OTP bots and challenges in detecting real-time attacks make mitigation efforts increasingly difficult.
🛡️ Bypassing Two-Factor Authentication (2FA)
OTP bots exploit vulnerabilities in 2FA systems, making it easier for attackers to gain unauthorized access to accounts even with an added security layer.
💳 Account Takeover
Attackers use OTP bots to take control of user accounts, leading to identity theft, financial fraud, or misuse of sensitive information.
💸 Financial Losses
OTP bots are often used to drain bank accounts, make unauthorized purchases, or transfer funds fraudulently.
🏢 Reputation Damage
Businesses targeted by OTP bot attacks risk losing customer trust, resulting in reputational harm and potential loss of business.
🔓 Security Breaches
With access to accounts, attackers can extract personal or business information, leading to further breaches or data leaks. These bots can automate and execute attacks at scale, compromising multiple accounts in a short amount of time.
💼 Increased Costs for Businesses
Organizations face higher expenses for recovery, fraud prevention, and implementing advanced security measures post-attack.
🔐 Undermining Confidence in Security Systems
Frequent successful attacks may discourage users from relying on 2FA systems, undermining overall trust in digital security.
Mitigating OTP Bot Risks with SuperTokens
Password Breach Detection
The first step in an OTP bot attack is the hacker having the user’s credentials, like a password. Preventing password leaks stops the attacks before they even have a chance to begin. Password breach detections checks passwords against a database of leaked passwords to see if they’ve been leaked before. This helps keep accounts safe by avoiding weak passwords.
Password breach detection prevents OTP bot attacks at the source by ensuring users do not use previously leaked passwords, cutting off the attack before credentials are compromised.
Bot Detection
Bot detection identifies and prevents automated scripts or bots from performing malicious activities such as credential stuffing, account takeover attempts, or scraping sensitive data. It uses advanced algorithms to analyze user behavior, request patterns, and other indicators to distinguish between human users and automated bots.
By identifying and blocking automated scripts, bot detection stops OTP bots from initiating login attempts or exploiting vulnerabilities.
Suspicious IP Detection
Suspicious IP detection finds suspicious IP addresses that are known for malicious activities. This includes detecting the use of VPNs, TOR, proxy servers, or other network configurations that may be used to hide the user’s true location or identity.
Suspicious IP detection prevents OTP bots by flagging and blocking requests from high-risk IP addresses often associated with malicious activities.
TOTP Authentication
TOTP (Time-Based One-Time Passwords) is a two-factor authentication method designed for high-security scenarios, particularly for sensitive use cases like financial transactions in fintech or cryptocurrency platforms, or accessing company HR or payroll systems. It requires users to prove possession of their device by generating a unique code that changes every 30, 60, or 90 seconds.
TOTP authentication strengthens defense against OTP bots by requiring time-sensitive, device-generated codes, making it nearly impossible for attackers to intercept or reuse the authentication tokens.
Conclusion
OTP bot cybercriminals might be clever, but we’re smarter. While Two-Factor Authentication (2FA) is still one of the best defenses out there, it’s clear that we need to stay sharp and keep evolving our security game.
Understanding how OTP bots work is the first step to beating them. The next? Using tools like SuperTokens to stop them in their tracks. Whether it’s detecting bots, flagging suspicious activity, or upgrading to TOTP, there’s no shortage of ways to fight back.
So, don’t wait for trouble to knock on your door. Strengthen your defenses, stay alert, and keep your accounts, and your peace of mind, secure. We’ve got this. 💪🔐

