JWT Decoder
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),)
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),)
JSON Web Token is an open industry standard used to share information between two entities.
They contain JSON objects which have the information that needs to be shared. Each JWT is also signed using cryptography to ensure that the client or a malicious party cannot alter the JSON contents.
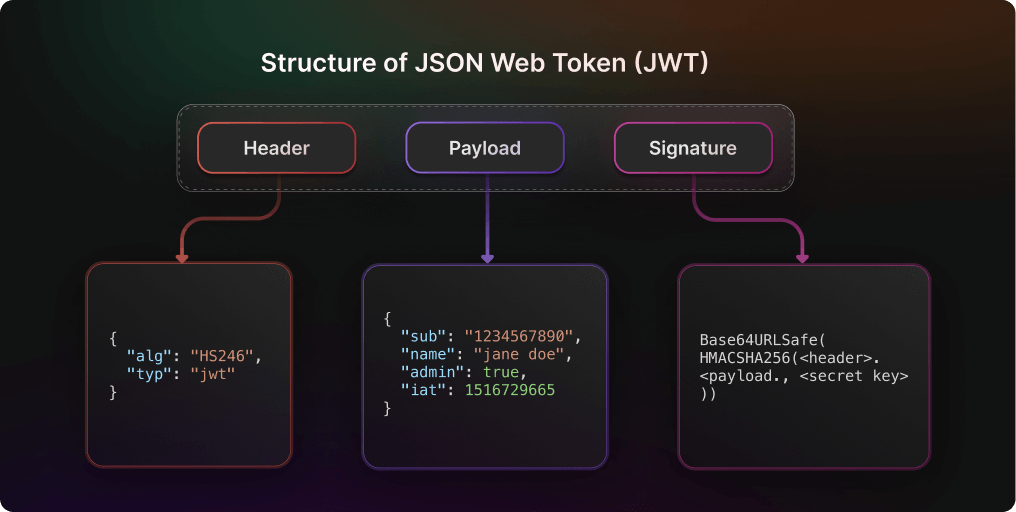
A JWT contains three distinct parts that work together to create a secure, self-contained token. These parts are separated by dots (.) and each serves a specific purpose in the token's functionality and security. The three parts are:
The header contains metadata about the token. It consists of two parts:
The payload contains the claims or the JSON object. It is a JSON object that is encoded using Base64Url encoding.
A string that is generated via a cryptographic algorithm that can be used to verify the integrity of the JSON payload.
When users report issues with login or permissions, decoding the JWT reveals critical claims like exp (expiration), iss (issuer), aud (audience), and scope or roles. This inspection helps identify issues like expired tokens, incorrect issuers, or missing permissions—before they lead to broken workflows.
JWTs contain structured claims that reveal user roles or privileges. Developers decode access tokens during runtime to populate UI features (e.g., showing admin-only options) or enforce backend ACLs based on claims such as roles or scope.
Never rely on decoded data alone. Always verify the signature to ensure the token wasn't forged or tampered with.
Decoding without verification can expose you to:
You can find our complete guide on how JWT works and how you can generate JWTs in this blog.