OAuth is a powerful and flexible protocol for authorization. To understand its technical aspects better, it’s important to dive into its details, explore its flows with diagrams, and see real-world examples of OAuth in action.
Table of Contents
- What is OAuth and Why is it Important?
- The OAuth Flow: A Step-by-Step Walkthrough
- Examples of OAuth applied in Various Scenarios
- Conclusion
What is OAuth and Why is it Important?
OAuth is an open standard for access delegation commonly used as a way to grant websites or applications limited access to a user’s information without exposing passwords. It plays a crucial role in modern web and mobile applications by enabling secure authorization.
Evolution of OAuth
OAuth has evolved from its inception to its current version, OAuth 2.0. The original OAuth 1.0, though revolutionary, had several limitations, such as the complexity of obtaining request tokens and exchanging them for access tokens. OAuth 2.0, on the other hand, simplified this process and introduced the use of access tokens and refresh tokens.
OAuth 1.0 vs OAuth 2.0
- OAuth 1.0: Introduced the concept of access delegation but was complex and had significant limitations.
- OAuth 2.0: Simplified the process, introduced access and refresh tokens, and made it easier to implement.
| Feature | OAuth 1.0 | OAuth 2.0 |
|---|---|---|
| Token Types | Request token, Access token | Access token, Refresh token |
| Complexity | High | Low |
| Security | Signed requests | Bearer tokens |
| Flexibility | Limited | Highly flexible |
| Grant Types | Single grant type | Multiple grant types |
The OAuth Flow: A Step-by-Step Walkthrough
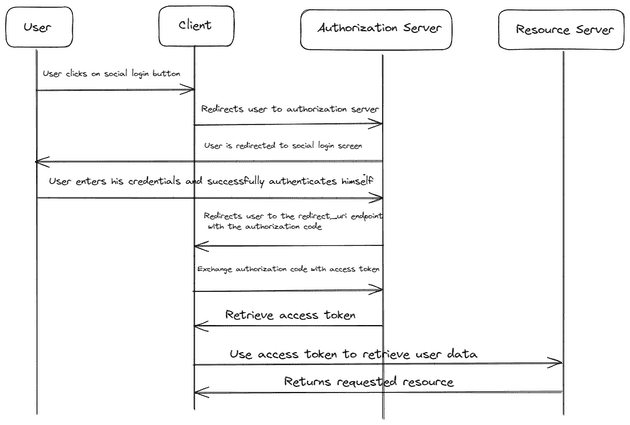
Understanding the OAuth flow is crucial for implementing and troubleshooting OAuth-based systems. Here, we provide a detailed walkthrough of the OAuth authorization process with diagrams.
Authorization Code Grant
The Authorization Code Grant is the most common OAuth 2.0 flow. It is used by web applications and involves the following steps:
- User Authorization: The user is redirected to the authorization server to grant access.
- Authorization Grant: If the user grants access, the authorization server redirects the user back to the client with an authorization code.
- Access Token Request: The client requests an access token from the authorization server using the authorization code.
- Access Token Response: The authorization server responds with an access token.
Implicit Grant
The Implicit Grant is used for client-side applications where the client directly receives the access token without an intermediate authorization code.
- User Authorization: The user is redirected to the authorization server to grant access.
- Access Token: If the user grants access, the authorization server redirects the user back to the client with the access token in the URL fragment.
Resource Owner Password Credentials Grant
This grant type is used when the user trusts the client with their credentials. The client directly receives the user’s credentials and exchanges them for an access token.
- Credentials Submission: The client collects the user’s credentials and sends them to the authorization server.
- Access Token Response: The authorization server validates the credentials and responds with an access token.
Client Credentials Grant
The Client Credentials Grant is used for server-to-server communication where the client uses its own credentials to obtain an access token.
- Token Request: The client sends its credentials to the authorization server.
- Token Response: The authorization server validates the client’s credentials and responds with an access token.
Device Code Grant
The Device Code Grant is used for devices with limited input capabilities. It involves the following steps:
- Device Authorization: The device requests authorization from the authorization server and receives a device code.
- User Authorization: The user visits a URL on a different device, enters the code, and grants access.
- Access Token Request: The device polls the authorization server until the user grants access.
- Access Token Response: The authorization server responds with an access token once access is granted.
Examples of OAuth applied in Various Scenarios
OAuth can be applied in various scenarios, from single sign-on (SSO) to granting third-party applications access to user data. Here are some examples:
Single Sign-On (SSO)
Single Sign-On allows users to log in to multiple applications with a single set of credentials. For example, logging into a new application using Google. This reduces the need to remember multiple passwords and improves the user experience.
Third-Party Application Access
OAuth enables third-party applications to access user data on behalf of the user. For example, a social media management tool accessing your Twitter account to schedule posts.
API Access
APIs often use OAuth to secure access. For example, a weather application using OAuth to request weather data from a weather API.
Conclusion
OAuth is a versatile and essential protocol for modern web and mobile applications. It enables secure authorization and access delegation, improving both security and user experience. Understanding the different OAuth flows and how to apply them in various scenarios is crucial for developers.
To implement OAuth using SuperTokens, check out our documentation. For further reading, you can explore our blogs on OAuth vs JWT, OAuth vs OIDC, and OAuth 2 vs Session Management.
For more information on OAuth, visit Wikipedia or check out this simple explanation on Stack Overflow.