Introduction
Overview
The Attack Protection Suite feature identifies and prevents suspicious activities in authentication sessions. It leverages detection methods to enhance the security of your application.
This feature is in beta and not enabled by default. Check the quickstart guide for instructions on how to set it up.
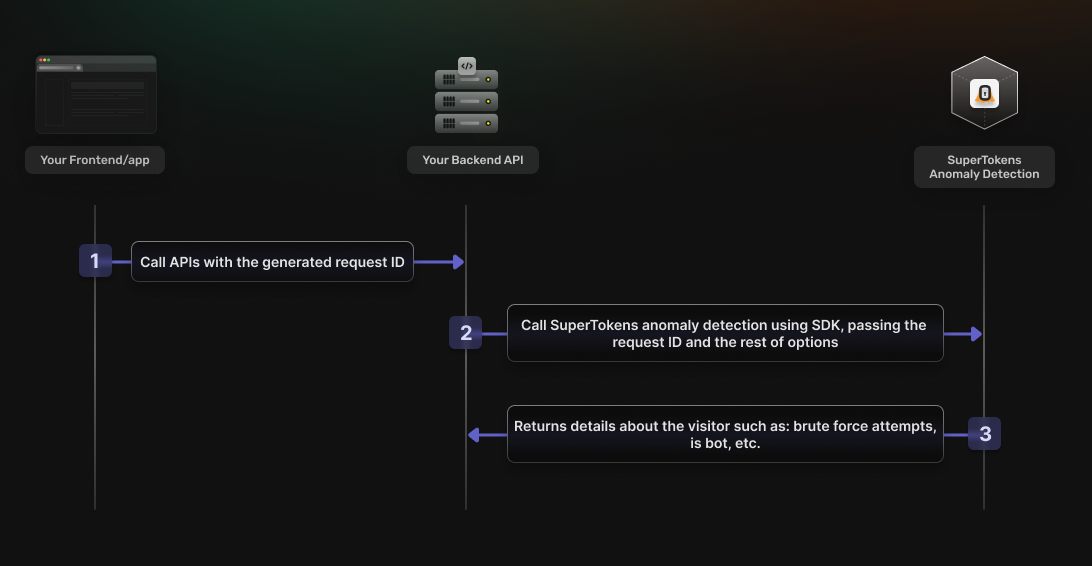
The feature processes requests and provides risk assessments. You can use these assessments to enforce additional security measures, such as requiring two-factor authentication for suspicious logins or blocking high-risk attempts altogether. Check the next diagram for a high-level overview of how the feature's flow works.
Features
-
Brute Force Attack Detection: Watches how many times someone tries to do a specific action (such as logging in, resetting password, etc.) within a certain time. If there are too many attempts, it stops them to prevent bad actors from compromising accounts.
-
Password Breach Detection: Checks passwords against a database of leaked passwords to see if they have leaked before. This helps keep accounts safe by avoiding weak passwords.
-
Impossible Travel Detection: Identifies fraudulent login attempts by detecting geographically impossible travel between user sessions in a short time.
-
Bot Detection: Identifies and prevents automated scripts or bots from performing malicious activities such as credential stuffing, account takeover attempts, or scraping sensitive data. It uses advanced algorithms to analyze user behavior, request patterns, and other indicators to distinguish between human users and automated bots.
-
Suspicious IP Detection: Detects suspicious IP addresses known for malicious activities. This includes detecting the use of VPNs, Tor, proxy servers, or other network configurations that may hide the user's true location or identity.
-
New Device Detection: Recognizes when a user logs in from a new, previously unseen device. This helps find possible unauthorized logins.
-
Device Count Tracking: Monitors the number of unique devices associated with a user account. This helps spot unusual account use.
-
Requester Detection: Recognize and remember devices and requester details, even when they try to disguise themselves. This helps track and identify the same device or requester across multiple login attempts, improving security and user recognition.
Getting started
To learn how to use the feature in your application open the quickstart guide.
Use the feature only with either the Email Password or Passwordless authentication recipes. For social or enterprise login, it is not needed.