SuperTokens Blog

March 20, 2024
FedCM and how OAuth Flows are affected in the Post-Third-Party Cookie Era
Third Party Cookies have been synonymous with user tracking and privacy issues. In 2021 Google put forth a plan to retire third party cookies from chromium based browsers and put for the FedCM APIs. In this blog we will be discussing this change and what it means for traditional OAuth flows.

March 13, 2024
Phishing Attacks in 2024
Over the years phishing attacks have become more sophisticated than ever. In this blog we break down how phishing attacks have evolved and how you can safeguard against them
March 07, 2024
The difference between OTP, TOTP and HOTP
One time passwords are a more secure method of authentication. They remedy a number of issues which plague traditional username-password based authentication. But with methods like TOTP and HOTP it can be confusing. In this blog we break down these methods with their benefits and downsides

February 23, 2024
Understanding Authorization code flow with PKCE
Federated identity with OAuth is one of the most popular methods of implementing authentication. It lowers sign-up friction and is more secure than other auth methods like email-password based authentication.

February 20, 2024
All You Need To Know About the Zero Trust Model
Zero Trust is an IT security model that emphasizes identity verification for every person or device trying to access resources on a private network. In this blog we go over it's core principles and practical benefits.

February 16, 2024
What is SCIM Provisioning?
Managing identities can be a pain, in the past administrators would have to manually add identifying information needed by applications about users. This process takes longer and has a high margin of error. SCIM streamlines the management of user groups and devices. In this blog we will explore how it works.
February 13, 2024
What is Credential Stuffing?
Most people are familiar with brute force attacks, where attackers attempt to guess passwords using characters at random paired with common password suggestions, but what is Credential Stuffing? In this we will go over this type of attack and how you can safeguard against it.
January 30, 2024
Navigating the Complex World of CAPTCHA Technology in Authentication
What is Captcha? Why is it needed? In this blog we will answer these questions and more

January 17, 2024
Unveiling the Intricacies of Local Storage and Session Storage
In this blog we delve into the workings of Local and Session storage breaking down the nuances that set them apart
January 16, 2024
Demystifying SAML: A Comprehensive Guide
SAML is an authentication standard created to address the growing need of federated identity. In this blog we go over what SAML is and what makes it special.

January 10, 2024
The Multifaceted Benefits of Multi-Factor Authentication
Traditional login mechanisms are plagued by security vulnerabilities and are susceptible to attacks. Multi-factor authentication bolsters security and mitigates a number of these vulnerabilities and has now become an industry standard.
December 11, 2023
Access Control for modern web applications
Access control plays a key role in protecting our data as we progressively move into an online society. In this blog we will explore the different types of access control and how they safeguard against attackers.
December 01, 2023
Multi-Tenant Authentication in 2024
Multi-tenant systems allow a single instance of a software application to serve multiple different tenants. This allows for a number of benefits that will be explored in this blog

November 16, 2023
What is TOTP and why do you need it?
Time based one-time passwords solve a number of issues that plague traditional authentication methods. In this blog we break down TOTP and why it's so useful.

October 23, 2023
Adding login to your Next.js app using the app directory with SuperTokens
This blog explains how to setup email password and social login with SuperTokens using the app directory in Next.js.

October 01, 2023
How we used multi-tenancy to cut our AWS costs by 50%
Part 2 in a series of howe we were able to cut down our AWS infrastructure costs by more than 50%
September 28, 2023
How to create an invite-only auth flow in 2023
Invite only flows can drive exclusivity and enhance user engagement. In this blog we will go over how you can customize SuperTokens authentication to create an invite only flow
September 19, 2023
How we cut our AWS costs by more than 50%
Part 1 in a series of how we were able to cut down our AWS infrastructure costs by more than 50%
September 04, 2023
What is LDAP & How does it work?
In workforce identity and B2B flows, LDAP is main protocol used to interact with directory services that store user identity and device information. In this blog post we take a look at LDAP and how it works.
September 01, 2023
Demystifying HTTP Error Codes 401 vs 403
In this blog we will go over the http protocol error codes 401 and 403 and describe when is it appropriate to use each of them.

August 16, 2023
URI vs URL: The real difference between the two
In this blog we break down the differences between URL, URI, and URN

August 12, 2023
Why did HashiCorp adopt the Business Source License?
What is the Business Source License and why did HashiCorp adopt it?
August 08, 2023
Understanding JWKS (JSON Web Key Set)
JWKS are an important part of the authentication process. In this article we go over what they are and how they are used

August 02, 2023
Authentication vs Authorization: What's the difference?
Authentication and Authorization represent two fundamentally different aspects of security that work together in order to protect sensitive information. In this blog, we will go over some of the key differences between the two.

July 25, 2023
SAML vs OAuth: Choosing the right protocol
SAML and OAuth are protocols often used in the authentication but what are the differences between them and which one do you choose?

July 12, 2023
Migrating users without downtime in your service (The Lazy Migration Strategy)
User Migration can be a challenging process, in this article we go over some user migration scenarios and break down the lazy migration strategy
June 23, 2023
How we built a Chatbot that is an Expert at SuperTokens
Learn how we built a Q&A bot that is an expert at SuperTokens powered by ChatGPT

June 08, 2023
Ory vs Keycloak vs SuperTokens
Comparing the three leading open-source authentication providers - Ory, Keycloak and SuperTokens

April 17, 2023
OIDC vs OAuth
We break down the OIDC and OAuth standards and explain the key differences between the two

April 17, 2023
Testing SSO Implementation
A guide into single sign-on implementation and how to perform sso testing for authentication and login

March 16, 2023
Learnings from Revamping SuperTokens
A #buildinpublic piece on why we designed the SuperTokens homepage
March 06, 2023
Django Bootstrap Login Template (How-To)
This tutorial wil guide you on how you can setup a bootstrap login template in Django
February 24, 2023
Implementing the right Email Verification flow
Email verification can increase friction and adds another stop to onboarding, but when done correctly can lead to better security and establish better communication with users.
February 23, 2023
A Guide to Implementing Passwordless Login
Passwordless is one of the most popular authentication methods

February 03, 2023
Self-hosted Authentication
By self-hosting auth users gain finer control over their data.To shed some light on the matter, let’s compare several authentication providers which offer self-hosting functionality
January 16, 2023
Creating Great Authentication Experiences with Custom UI
A guide on creating great authentication experiences with custom UI
January 12, 2023
5 Tips for Optimizing Your React App’s Performance
Poor app performance can reduce user engagement and will negatively affect SEO, here are 5 tips to optimize your react app

January 11, 2023
What do pre-built authentication UIs look like?
A comparison of the pre-built UIs from current authentication providers and how to customize them

January 09, 2023
SuperTokens 2022 Year in Review
2022 had been an amazing year for SuperTokens, here are some of the top highlights

November 15, 2022
Auth0 Pricing: The Complete Guide [2022]
An in depth guide covering Auth0's pricing model

November 15, 2022
AWS Cognito Pricing: The Complete Guide [2022]
An in depth guide covering AWS Cognito's pricing model

November 15, 2022
Okta Pricing: The Complete Guide [2022]
An in depth guide covering Okta's pricing model
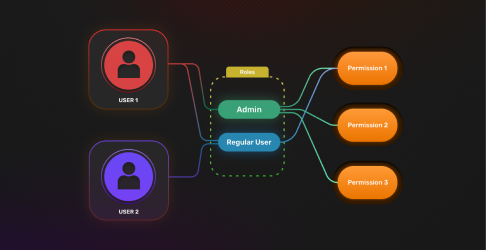
October 27, 2022
Introducing User Roles Authorization with SuperTokens
With user roles, you can now use SuperTokens to easily attach a different set of permissions to each user.
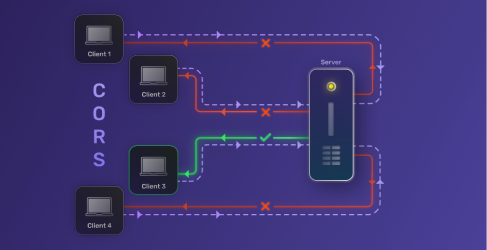
October 27, 2022
What is Cross Origin Resource Sharing (CORS)?
Cross-Origin Resource Sharing (CORS) is a mechanism that supports secure requests and data transfers from outside origins (domain, scheme, or port).
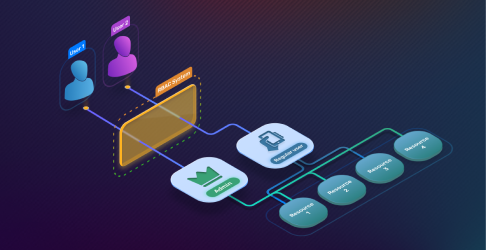
October 20, 2022
What is Roles-Based Access Control (RBAC)?
Learn about RBAC and advantages + disadvantages compared to ABAC.

September 12, 2022
Protecting your Supabase app with SuperTokens authentication.
When building an app with Supabase you will have to choose an authentication solution. Here are some reasons why you should choose SuperTokens as you auth provider and why it pairs so well with Supabase
August 17, 2022
How to use SuperTokens in a VueJS app with your own UI
Learn how to integrate supertokens-web-js SDK into your VueJS application.

July 26, 2022
Passwordless for Product Managers
A quick overview of different types of passwordless authentication methods to improve user retention

July 13, 2022
How to use SuperTokens' pre built UI with VueJS
A step by step guide on how to integrate SuperTokens' pre built UI in a VueJS app

May 09, 2022
Top Auth0 alternatives: Auth0 vs Okta vs Cognito vs SuperTokens [2023]
An in depth review of Auth0 alternatives for 2023: Auth0 vs Okta vs Cognito vs SuperTokens
April 24, 2022
How to connect SuperTokens to a MySQL or to a PostgreSQL database
Learn how to connect a self-hosted SuperTokens core to a database with or without Docker

April 14, 2022
How to deploy SuperTokens with React and NodeJS on Vercel
This tutorial wil guide you on how to add SuperTokens to a React and Express app deployed on Vercel

March 24, 2022
What is a JWT? Understanding JSON Web Tokens
Learn about JWTs, their pros & cons, and how they work.

March 23, 2022
OAuth vs JWT (JSON Web Tokens): An In-Depth Comparison
Learn about the difference between JWT Token and OAuth

March 14, 2022
Building a login screen with React and Bootstrap
Build an elegant login screen super fast using React and Bootstrap
March 02, 2022
What is Password Hashing and why is it important
A guide on password hashing and salting in different languages and why it's important to do so

February 10, 2022
Revoking Access to JWT tokens with a Blacklist/Deny List
Learn how to maintain a JWT token blacklist / deny list using an in-memory data cache
February 09, 2022
How to Set up Social and Email Password Login With ReactJS in 10 Minute
In this blog, we'll walk you through setting up an email-password authentication with popular social providers like Google, GitHub, and Apple using SuperTokens on a ReactJS application with ExpressJS as the backend.
January 26, 2022
Adding social login to your website with SuperTokens (custom UI only)
This blog walks you through integrating your frontend with social login APIs provided by SuperTokens.

December 13, 2021
How to customise SuperTokens APIs
Any auth solution must provide the ability to customise their APIs. In this blog we discuss how to customise the auth APIs provided by SuperTokens using its “Override” feature
November 11, 2021
Why is redux state immutable?
This blog covers an analysis of why redux state is immutable and how you should go about modifying state in your Redux applications

November 10, 2021
Solve the problem of vendor lock-in
What is vendor lock-in? How does it affect your customers? What are the different ways you can minimize it? Read the blog to learn more.

June 01, 2021
Implementing a forgot password flow (with pseudo code)
What should happen on the backend when a user forgets their password? Read to find a pseudo code implementation of the simplest way to reset passwords securely.

March 05, 2021
The real reason Okta spent $6.5B on Auth0
Why did Okta spend $6.5B on Auth0? What does this mean for app developers? See reactions from customers and employees

December 10, 2020
Speed up your web development time by integrating Webflow into a React application
Writing JSX to build pixel perfect UI elements can be very time consuming and frustrating. Learn how react engineers can inject complex elements / React components into a Webflow generated HTML page.
July 30, 2020
Detecting session hijacking using rotating refresh tokens - OSW 2020
Session hijacking is one of the oldest, yet unsolved, attack vectors to gain unauthorised access to a user’s account. This discussion is regarding a method called "rotating refresh tokens" to better detect token theft.

June 23, 2020
Cookies vs Localstorage for sessions–everything you need to know
Learn about the best approach and common misconceptions of storing sessions in cookies or browser storage

June 11, 2020
Express-session vs SuperTokens for handling user sessions
This article will be comparing SuperTokens to Node’s most popular session management library– express-session. Learn more about the comparison based on different security and performance metrics.
May 06, 2020
Should you use Express-session for your production app?
Being Node’s most popular session management library, express-session has its set of flaws– especially when it comes to security. This article will help you analyse the good and bad parts of it.

April 24, 2020
OAuth 2.0 vs Session Management
A lot of developers confuse OAuth with web session management and hence end up using the wrong protocol. This article will clarify when to use what solution.

March 18, 2020
Are you using JWTs for user sessions in the correct way?
JWTs were originally designed for use in OAuth. This article covers the pros and cons of using JWT and talks about a solution which has the advantages of JWTs without any of its disadvantages.
June 08, 2019
The best way to securely manage user sessions
This blog covers an analysis of a new open source session flow that is secure and easy to integrate. Learn more about the customizable library and its implementation details.
June 07, 2019
All you need to know about user session security
This article covers extensive conversations with over 70+ developers exploring different session management practices, identifying issues and converging on a solution to these issues.
